As I was writing this post, I received an email announcing that my application was accepted for my CWNE. I’ve been given the special CWNE #500!!!! That everyone had been anxiously awaiting.. since numbers are so important in this industry. I feel like I just joined a family of other CWNEs who have reach this status. This final post in the series is my thank you to the Wifi community! To the Future!!
To close off this blog series, I wanted to discuss clients. That half of the equation that has the biggest influence on our Wifi networks, but we, as educational entities or others, have little to no control over clients wanting to join our BYOD networks like eduroam or WPA3-SAE guest networks.
My previous posts covered:
- Issues with WPA3 and eduroam
- Possible solutions with protocol captures
- Options for deploying eduroam in 6ghz from different vendors
This final post in my series on eduroam and 6GHz will cover:
- What happens with Mac, Android, Windows, and Chromebook Clients that do not support WPA3-Enterprise and WPA3-SAE
- What happens with those clients with WPA3-Enterprise Transition Mode and WPA3-SAE Transition Mode
- WPA3-Enterprise and WPA3-SAE “Downgrade Protections”
I put the test results from all the devices I discuss below and others in an executive summary on this blog post. I know this post is extremely long and view it as a reference.
What follows are specific devices that others have posted about, or I have personally tested. The rest of this post will dig into the following clients and how they handle WPA3-SAE, WPA3-Enterprise, WPA3-SAE Transition, and WPA3-Enterprise Transition. Let’s dig into the test results!
- 2013 MacBook Pro
- 2013 MacBook Air
- 2012 MacBook Pro
- iPod Touch Gen 2
- iPhone 6
- iPad Mini Gen 1
- Apple TV Gen 3
- Windows Surface RT
- Toshiba L775
- Samsung Galaxy Note 3
- Google Nexus 7
- Acer Chromebook 11 (CB3-111)
- Asus Chromebox CN60

I’m going to expand this post to include WPA3-SAE and not just focus on eduroam. The main focus is still eduroam, but I’ll include how the clients interact when connecting to a WPA3-SAE and WPA3-SAE Transition networks.
Although I test specific devices below, my goal is to explore how client types handle the different security types. The results won’t cover every device and operating system versions. I don’t have an unlimited number of old devices to test with. My testing is an expansion of testing that Jennifer Minella (JJ) and James Garringer performed at WLPC Phoenix 2023. Check out my previous posts in this series for details.
We most likely won’t be installing eduroam on IOT type devices. So, I’m limiting my testing of end user devices to those most likely to be joining our eduroam networks, Windows, Mac, Android, iOS, iPadOS, and Chromebooks. Most non-IOT type newer operating systems and devices are going to support WPA3-Enterprise and WPA3-SAE. My focus is on devices that DO NOT support those security types.
That said, I cannot blankly say that every device running a certain version of an operating system (outside of Apple) will support WPA3-Enterprise, WPA3-SAE, and the Transition Modes. In my research many types of Chromebooks and Windows didn’t support WPA3-SAE at one point, but do with updates. I don’t have every type of devices, with my limited budget, to test to make sure the vendors are not doing something with the drivers that causes issues. That is why Transition Mode is still relevant on eduroam networks.
WPA2/WPA3 Enterprise Transition Client Support
There has been a lot of requests to find, specifically, which clients struggle with WPA3-Enterprise Transition, Full WPA3-Enterprise, WPA3-SAE Transition, and Full WPA3-SAE. I don’t have an exhaustive list, but have found devices from each operating system. Thanks to the work of Wes Purvis, Jennifer (JJ) Minella, Peter Mackenzie, James Garringer, Gertjan Scharloo, Doug Hales, and others we have made some progress. All credit for the majority of my understanding on this topic goes to Wes, JJ, Peter, and James and from just playing with it in my own labs.
At WLPC Phoenix 2023, JJ presented a Deep Dive on WPA3 Migrations. During that deep dive, they dove into clients and how they are handling the transition. She recently released her findings in a blog post on her website SecurityUncorked.com. I HIGHLY recommend you go read her post!! It will contain way more details than I will get into here.
I also HIGHLY recommend that anyone interested in this topic go and purchase JJ’s Book, Wireless Security Architecture: Designing and Maintaining Secure Wireless for Enterprise. BUY IT ALREADY!!! (And no I don’t get ANY kick back for recommending it, I’m just a big fan!!)
This post will be building on the foundations of what others have discovered. My focus is specifically on WPA3-Enterprise with eduroam. JJ’s post focuses on client support on both WPA3 and WPA3-Enterprise. So, let’s dig into eduroam specifically.
JJ’s Recommendations and Findings
JJ’s blog post says the following specifically about WPA3-Enterprise:
“5. RECOMMENDATION: WPA-Enterprise (802.1X networks). Most 802.1X-capable endpoints are user-based and receive firmware updates regularly, meaning most endpoints connecting to these Enterprise networks will be able to connect to WPA3-Only networks without intervention. It is possible some endpoints haven’t received updates, and of course this is very likely in high BYOD environments such as colleges and universities. In these instances (and in favor of caution), it’s recommended to convert your existing WPA2-Enterprise network to a WPA3-Enterprise Transition Mode and monitor, then address/update endpoints connecting on WPA2. Once endpoints are all connecting with WPA3, it is then safe to migrate/upgrade that WLAN to WPA3-Enterprise Only.”
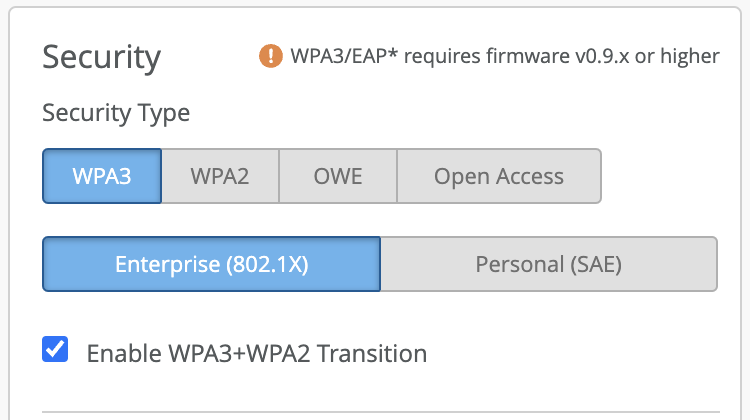
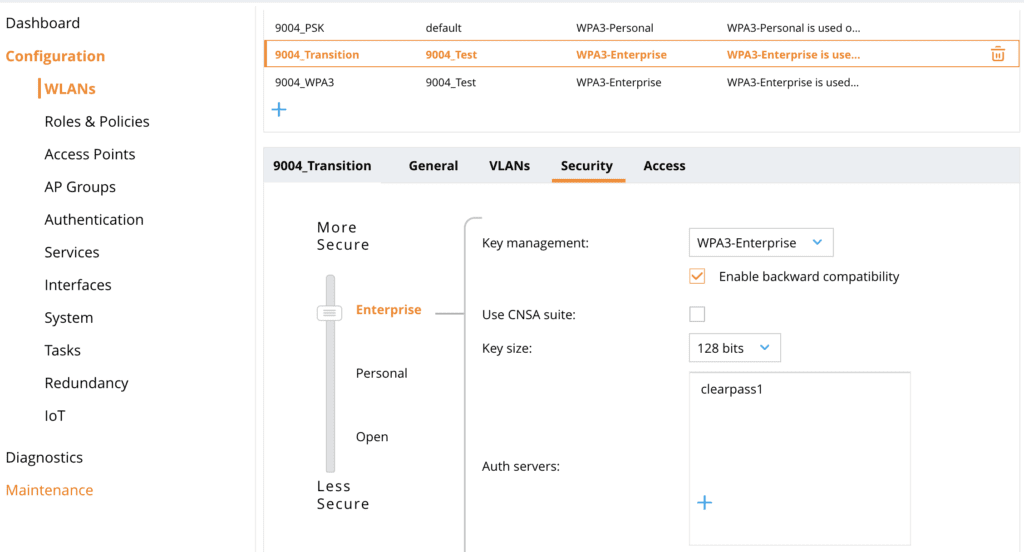
The one issue with just enabling Transition Mode is that WPA3-Enterprise Transition Mode is not available for all vendors when you enable Wifi 6e 6GHz on your eduroam SSID network as I talked extensively about in my last post. Juniper Mist and HPE Aruba have added WPA2/WPA3-Enterprise Transition Mode or “Compatibility Mode” as a checkbox. Everyone else from my testing, doesn’t yet give you this option. HOPEFULLY THIS CHANGES!!! Refer to my previous posts for in depth resources on those topics.
WPA3-Enterprise Client Testings
My thinking about this topic made me debate attending JJ’s Deep Dive at WLPC Phoenix 2023. During that deep dive, JJ had everyone, that attended, bring a vast selection of clients to test with WPA3. James Garringer from Apple took that to heart and brought a bunch of Apple devices to test. Because of their findings, Keith Parsons had JJ and James Garringer give a special presentation about their findings during the main sessions. Sadly, the video wasn’t released with the WLPC Presentations on Youtube, but you can find a summary on JJ’s blog I linked to previously. As I mentioned in my second part of this series, JJ and James talked about devices not liking multiple AKMs.
Apple Devices
To summarize their presentation and my previous post, James and JJ said that Apple iOS devices running iOS 11.2 or older wouldn’t connect to a Full WPA3 SSID. James further said that iOS 11.2 was released in June 2018 running on the iPhone 7 or older. Protected Management Frames (where the issues with WPA3-Enterprise comes in) was introduced in the iPhone 6 or newer. So, anyone with Apple devices trying to connect to our eduroam networks on the Legacy 2.4/5GHz bands using an iPhone 6 or older running iOS 11.2, if we implement WPA3-Enterprise, are not going to connect.
In my discussion with James, he shared with me this document from Apple that spells out what devices support WPA3 and PMF.
As I referenced in Part 2, Gertjan Scharloo‘s response to Doug Hales’ tweet said the following:
MacBook Air with MacOS Catalina 10.15.6

WPA3-Enterprise and WPA3-SAE
Gertjan mentions specifically macOS Catalina 10.15.7 running on a MacBook Pro. I happen to have an old MacBook Air that is running an even older version, 10.15.6. I thought it would be an excellent test device to show a device not connecting since he referenced a newer version. I was wrong.
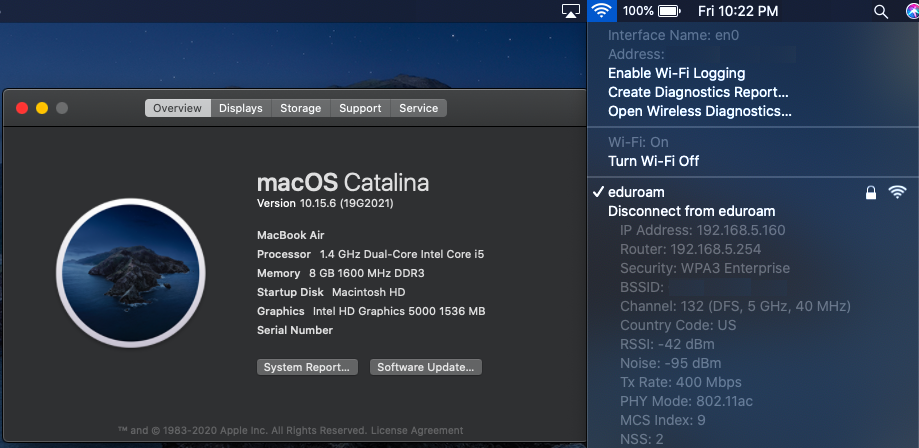
I installed my eduroam credentials, and it authenticated and joined without issue to a full WPA3-Enterprise Only SSID on 5GHz. I have the eduroam SSID configured to be full WPA3-Enterprise 802.11r FT on both 5GHz and 6GHz without the Dual SSID Profiles workaround. I later removed the 802.11r FT from the configuration to ensure Fast Transition wouldn’t cause connectivity issues for clients.
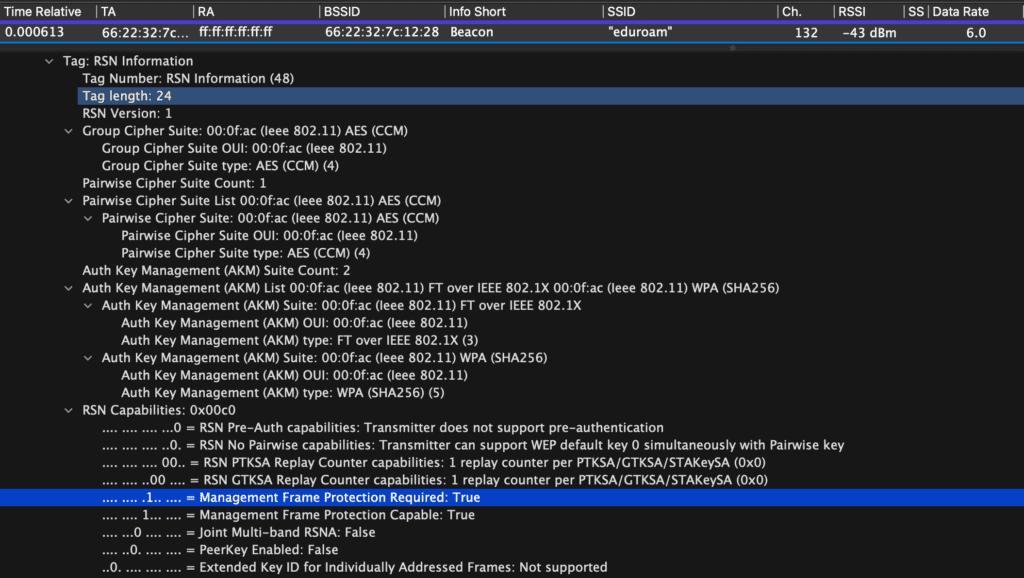
I was curious if the issue with MacOS Catalina was an issue with WPA3-SAE. So, I connected my MacBook Air to my home network that is set to WPA3-SAE Only. The device connected without issue, just like it had connected without issue to eduroam with WPA3-Enterprise only.
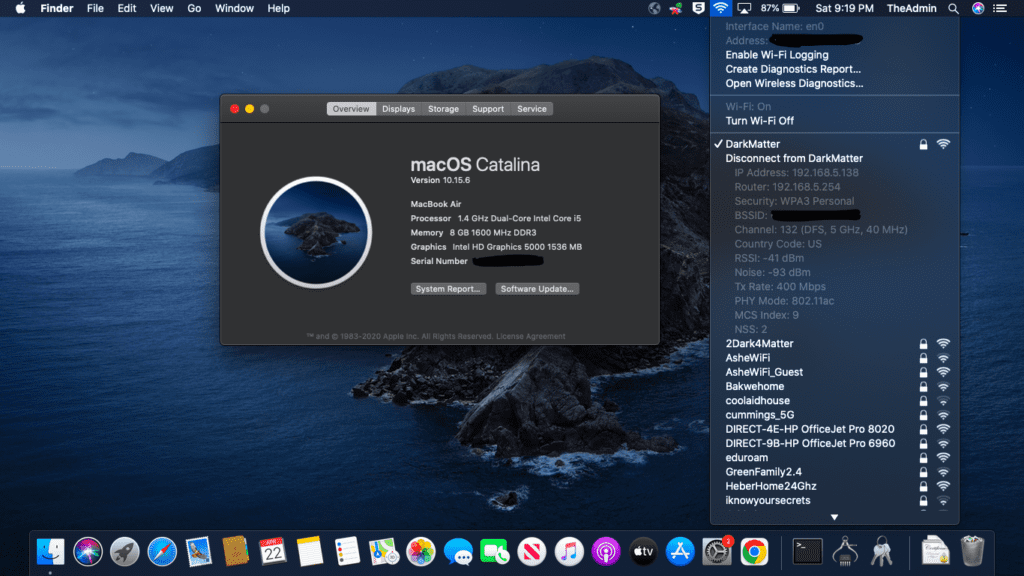
This made me wonder if the issue is hardware or software based. I wonder if Gertjan’s device truly didn’t support WPA3-Enterprise or not. My guess is that it does support WPA3-Enterprise and WPA3-SAE. His devices is a year newer than my test MacBook Air that does connect and it is running a newer version of Mac OS X than mine. From everything that I’ve read from other’s tests, this is just a software limitation. My tests below confirm that it’s a software limitation.
While specific to WPA3 and not WPA3-Enterprise, the Apple documentation says that WPA3 is supported on the following Apple devices:
- iPhone 7 or later
- iPad 5th generation or later
- Apple TV 4K or later
- Apple Watch series 3 or later
- Mac computers (late 2013 or later, with 802.11ac or later)
Since the differences between WPA2-Enterprise and WPA3-Enterprise is 802.11w Protected Management Frames (PMF). That Apple Documentation says PMF is supported on the following list:
- Phone 6 or later
- iPad Air 2 or later
- Apple TV HD or later
- Apple Watch series 3 or later
- Mac computers (late 2013 or later, with 802.11ac or later)
The Apple documentation doesn’t dig into specific software versions, instead they focus on devices. Basically, this list of devices all support a version of iOS, iPadOS, MacOS, tvOS, and WatchOS that does support WPA3 and PMF. Older OS versions on these devices MAY NOT support WPA3-Enterprise. The solution is simple for those devices in the lists or newer, just upgrade them to the latest version, and you should be good to go.
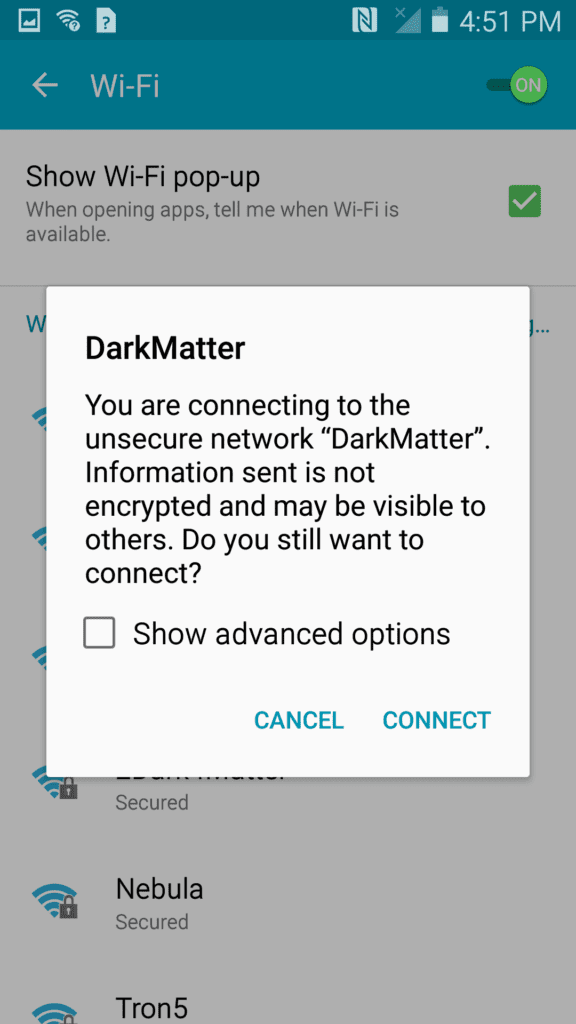
2012 MacBook Pro with Mac OS X El Capitan
Since my first attempt to find a device didn’t work as I expected. I decided to look even harder. I needed to find a device that I could guarantee that it didn’t support WPA3-Enterprise.

I remembered that I had an old MacBook Pro from Mid 2012 that falls below that line in that document from Apple for not supporting PMF or WPA3. It’s running MacOS X El Capitan 10.11.5. There’s no way this is going to support WPA3-Enterprise or PMF… So I installed my eduroam credentials and success (or failure)!!!! It wouldn’t join my eduroam WPA3-Enterprise Only network!!! It would join my eduroam WPA2-Enterprise Only network. So, I had my first working test device!!

WPA3-Enterprise Only
I was interested to see how Mac OS X would handle a AKM for a security type that it didn’t support or recognize. Interestingly enough, it treated it as a WPA2-Personal network NOT a WPA2-Enterprise network. It acted just like the Downgrade Protection Mechanisms included in WPA3-SAE; that I’ll talk about at the end of this post.
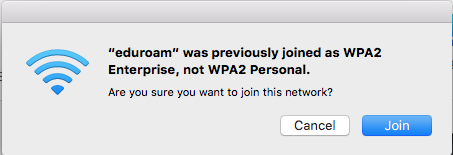
Since it didn’t recognize the AKM, Mac OS El Capitan tried to interpret it as best as it could. It knew that eduroam has been previously configured as WPA2-Enterprise, but it was interpreting this new WPA3-Enterprise network as configured as WPA2-Personal. If I chose to bypass that protection and clicked “Join”, it asks for a WPA2 password. Nothing that I enter there would work since the network is configured for an EAP-TLS Certificate instead of a password. It’s not a WPA2-PSK network.
WPA2/WPA3-Enterprise Transition Mode
I tested this MacBook Pro, and all my other devices, on Juniper Mist’s solution. If you haven’t read my previous blog post, Juniper Mist and HPE Aruba have a setting called “Enable WPA3+WPA2-Enterprise Transition” (Mist) or “Enable Backwards Compatibility” (Aruba). When checked, this setting turns on WPA2/3-Enterprise Transition Mode where PMF is not required but only capable on the 2.4/5GHz bands. This setting is not available on other vendors as my previous post explained.
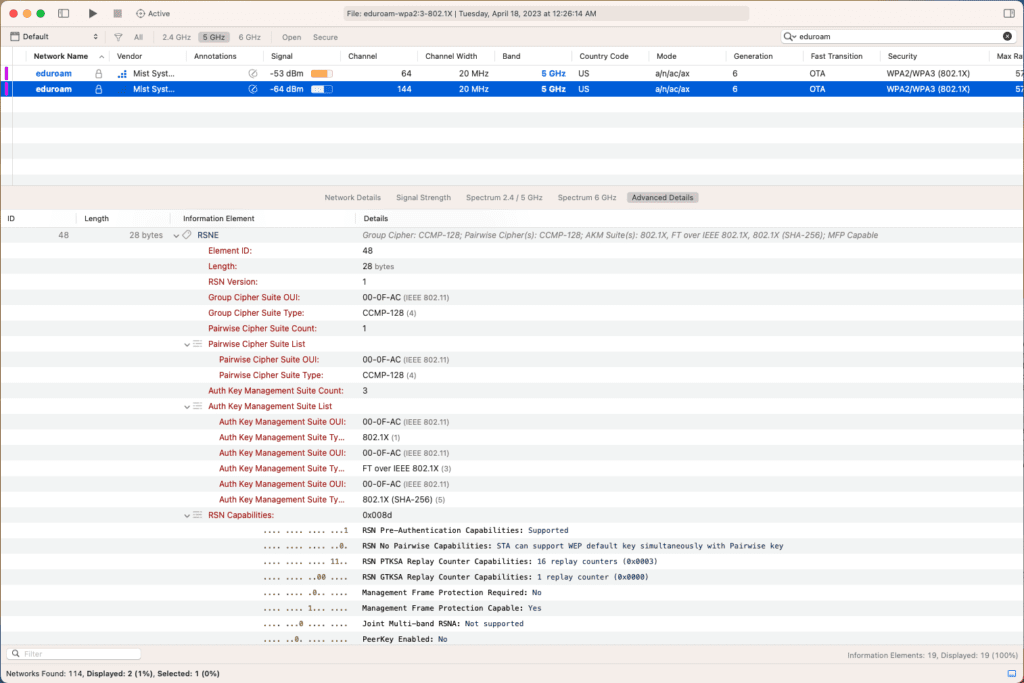
In my testing of this MacBook Pro that does not support WPA3-Enterprise, the device connected to eduroam without an issue when I enable that “WPA3 + WPA2 Enterprise Transition” checkbox within Mist. The setting is working as expected! I didn’t get the WPA2-PSK error as I had before when I set the eduroam SSID to WPA3-Enterprise only.
Wifi Explorer Pro 3 correctly identifies the security type as “WPA2/WPA3 (802.1X)”. The RSN Capabilities field shows the Management Frame Protection Required set to “No” and the Management Frame Protection Capable set to “Yes”. So the network is truly doing Transition Mode on the 5GHz band with 6GHz enabled. This old MacBook Pro can connect with Transition Mode even though it freaks out on full WPA3-Enterprise.
WPA3-SAE Only
I decided to test the device on WPA3-SAE since it’s almost guaranteed it doesn’t support it. I connected the 2012 MacBook Pro to my home SSID that is running WPA3-SAE Only. It immediately doesn’t recognize the AKM and interprets it as WPA2-PSK. It gives this message that it “requires a WPA2 password.”
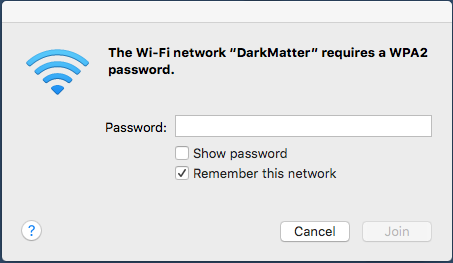
Unlike with my eduroam test above, I can enter a Passphrase since it is a WPA3-SAE network even though it says it “requires a WPA2 password”. So, I attempted to connect to it with my Passphrase for my home network. It tries to connect to the network but gave a “Connection failed.” error and never joined. The two technologies, WPA2 and WPA3, are different. PMK Keys are negotiated differently. So, a client that attempts to join a WPA3 network with WPA2 credentials is going to fail. Even if it’s the same password.
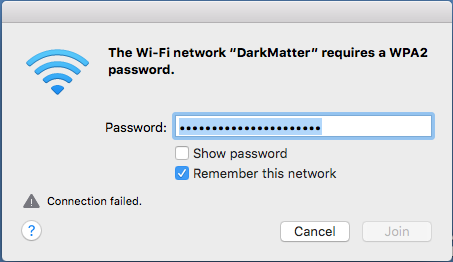
It didn’t show a Downgrade Protection Mechanism like before witih WPA3-Enterprise. It just tried to join the WPA3-SAE network with a WPA2-PSK password.
WPA2-PSK/WPA-SAE Transition Mode
Finally, I decided to test and see what the device would do with a WPA2-PSK/WPA3-SAE Transition Mode network. To not disrupt my existing network, I created a new SSID and enabled Transition Mode. It asked for the password as expected and showed the network as WPA2 as before. I entered the password and clicked Join.
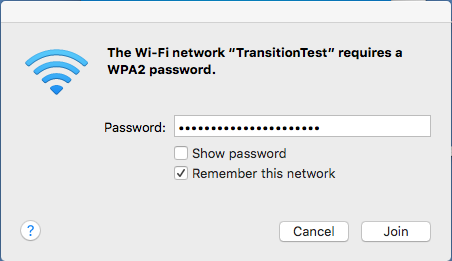
The 2012 MacBook Pro connected to the WPA2-PSK/WPA3-SAE Transition Mode network without an issue. So, WPA3 Transition Mode works!! It didn’t have any issues with multiple AKMs in the Beacon.
iPod Touch Gen 2
My buddy, Doug Hales, did some testing with WPA3-Enterprise. He found out that an old iPod Touch Gen 2 won’t connect. This would be similar to an iPhone since they run the same version of iOS minus a few apps like the Phone app. The original iPads were the same since they used to run iOS; until Apple broke them out into iPadOS in September 2019. Devices that run iPadOS are going to support both WPA3-Enterprise and PMF.
The results Doug shared on Twitter below are as I am seeing with all Apple devices that don’t understand the AKM. When an Apple device attempts to join the AKM it doesn’t understand for WPA3-Enterprise, it seems to treat it as a WPA2-PSK network. Doug’s picture below shows that same thing happening. It requests the user to “Enter Password” even though the network is an 802.1X SSID and not a PSK SSID.
The iPod Touch 2 only ran up to iOS 4.2.1 that was released in November 2010. iOS at that point supported 802.1X authentication but not WPA3-Enterprise or Protected Management Frames (PMF) as that didn’t come until a few years later. Apple’s Developer site says that EAP-TLS, EAP-PEAP or others are supported on iOS 4+ so the device should support the twenty year old WPA2-Enterprise. Older versions of iOS should also support 802.1X, but that’s not my focus of this post with such old devices.
Since the iPod Touch Gen 2 is SO old, even never versions of the iPod or the iPhone are not going to support WPA3-Enterprise, PMF, or WPA3-SAE. Apple’s documentation, I referenced before, says support started with the iPhone 6 for WPA3-Enterprise because of support for PMF and for the iPhone 7 for WPA3-SAE.
iPhone 6
My brother, a college student, was still using this iPhone 6 up until about a month ago but hadn’t installed the latest updates. Similar to the iPod Touch Gen 2, the iPhone 6 doesn’t support WPA3 after my testing. The official Apple documentation says that the iPhone 6 supports PMF, therefore supporting WPA3-Enterprise. It might need to be updated to support WPA3-Enterprise.

Interestingly, James Garringer said that Apple devices running iOS versions newer than iOS 11.2 should support WPA3. This iPhone 6 is running 12.5.5 so a newer version. My testing gave different results with this iPhone 6.
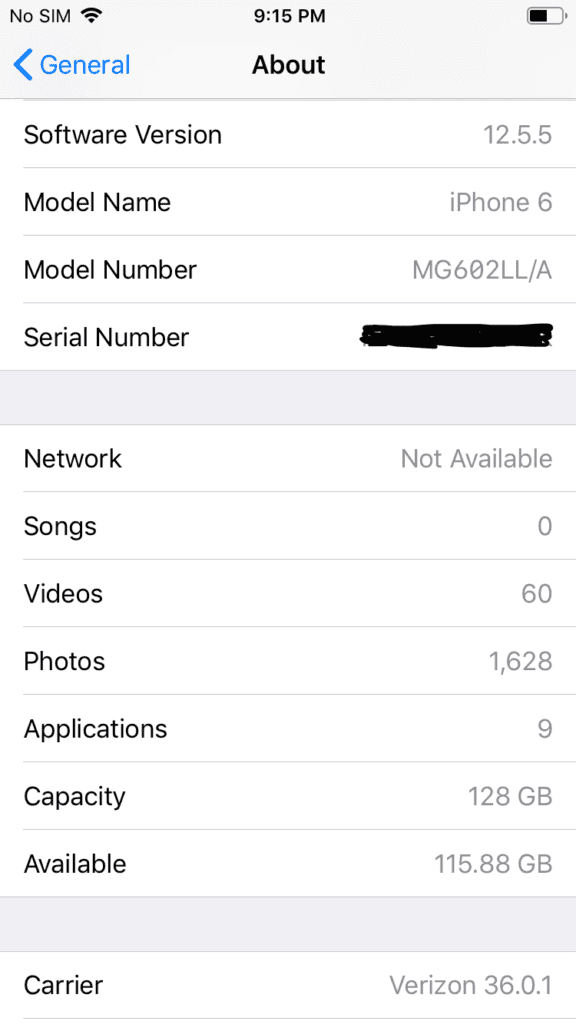
WPA2-Enterprise
First, just to setup a test, I connected the iPhone to eduroam with WPA2-Enterprise only. The iPhone connected without issues. So, once the control test was shown to be working, it was time to start my tests.
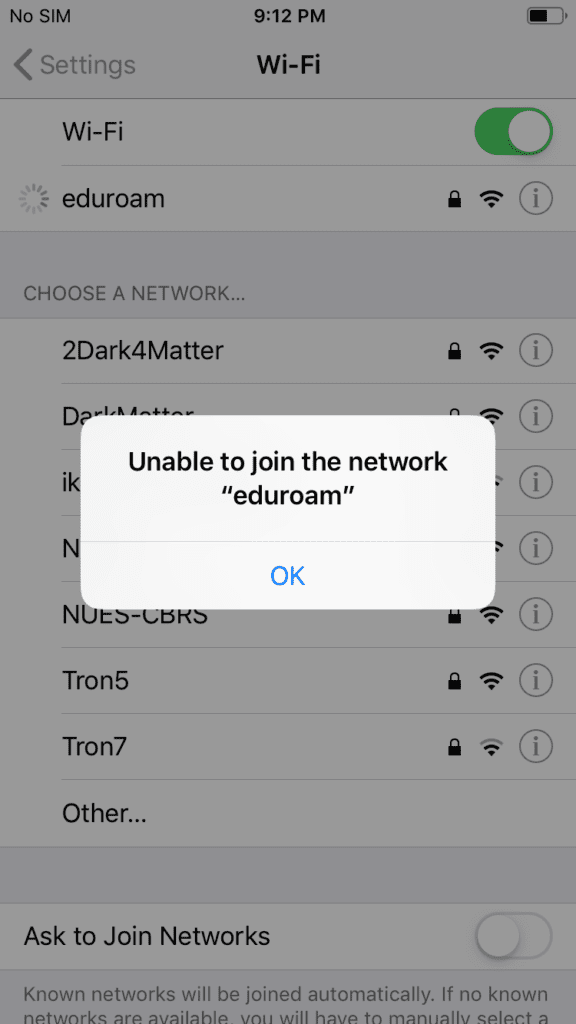
WPA3-Enterprise Only
First up, I set eduroam to be WPA3-Enterprise only. Unexpectedly, the iPhone 6 would not connect to eduroam. It gave a generic ‘Unable to join the network “eduroam”‘ error. Since the device didn’t understand the AKM for WPA3-Enterprise or support PMF it was unable to join the network. For older versions, this would be expected behavior when it doesn’t support WPA3. This is unexpected results for a iPhone 6 running 12.5.5 from the Apple Documentation and what James Garringer had shared.
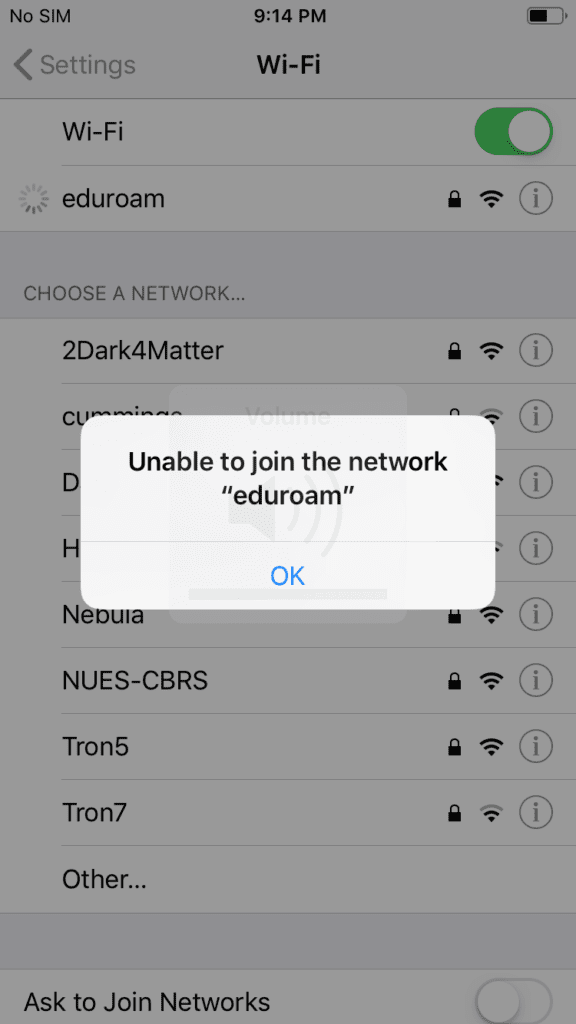
WPA2-Enterprise/WPA3-Enterprise Transition Mode
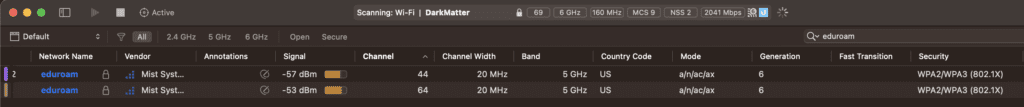
So, next I enable the WPA3-Enterprise Transition Mode in Mist. This result was very odd compared to all my other testing so far. The device would not join with Transition Mode enabled. It gave the same error as full WPA3-Enterprise.
Below is the results from Wifi Explorer Pro 3 showing that eduroam was configured with WPA2/WPA3-Enterprise Transition Mode. Very odd that the iPhone wouldn’t join this network, while most of the other devices that I have tested would connect without issue.
WPA3-SAE Only
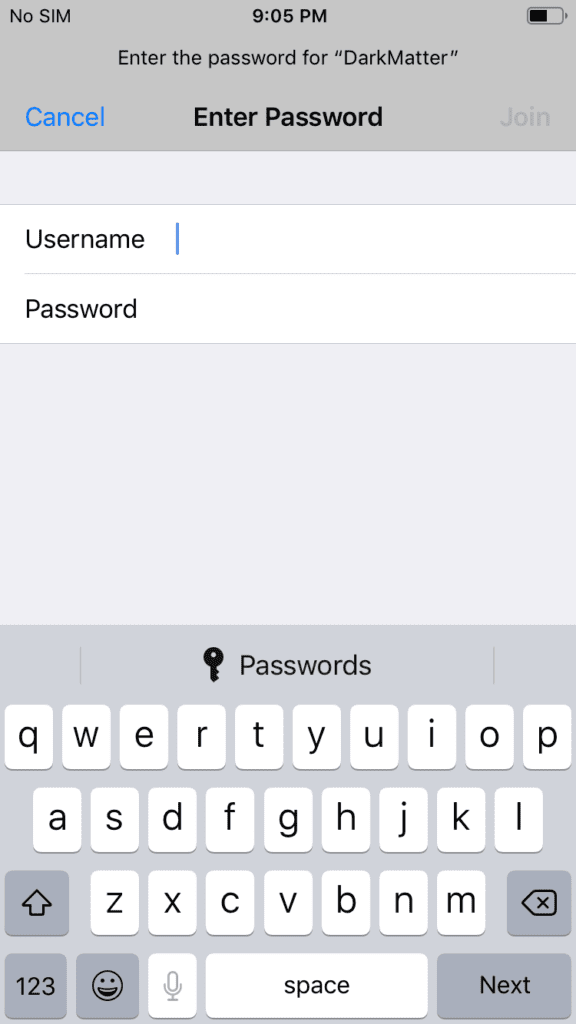
Next, I attempted to connect the iPhone 6 to my home network that is WPA3-SAE Only. Like before with eduroam, it unexpectedly would not connect. Instead of asking for a WPA3-SAE Password, it instead treated the SSID as a 802.1X network. It requested a username and password. Since the network is SAE and not 802.1X, nothing that I enter there is going to work. The iPhone doesn’t understand the AKM so it is attempting to interpret it however it can.
WPA2-PSK/WPA3-SAE Transition Mode
Lastly, I tried to connect the iPhone 6 to my test WPA2-PSK/WPA3-SAE Transition Mode SSID. This time, it didn’t have any weird results. The iPhone connected to the Transition Mode SSID without issues.
The iPhone gave some interesting results. Looking at the results others have shared and the official documentation, I expected this iPhone 6 to connect to the WPA3-SAE and WPA3-Enterprise network without issue. I was wrong. I was really surprised to see the iPhone 6 wouldn’t connect to the WPA2/WPA3-Enterprise Transition Mode network.
Ultimately, this brings up a good point. Even with documentation and other’s test results, you can’t guarantee a device is going to connect how you expect. Even though this iPhone didn’t connect with Transition Mode, an update should fix that issue, this is a big reason to enable Transition Mode on your eduroam networks that you cannot control. It provides the most backwards compatibility than just enabling full WPA3-Enterprise.
iPad Mini Gen 1
Next I had an old iPad Mini Gen 1 running iOS 9.3.5. I figure the device wouldn’t support WPA3-Enterprise and WPA3-SAE. I used a .mobileconfig file to setup the certificates. I connected it to eduroam and everything worked with WPA2-Enterprise.
WPA3-Enterprise Only
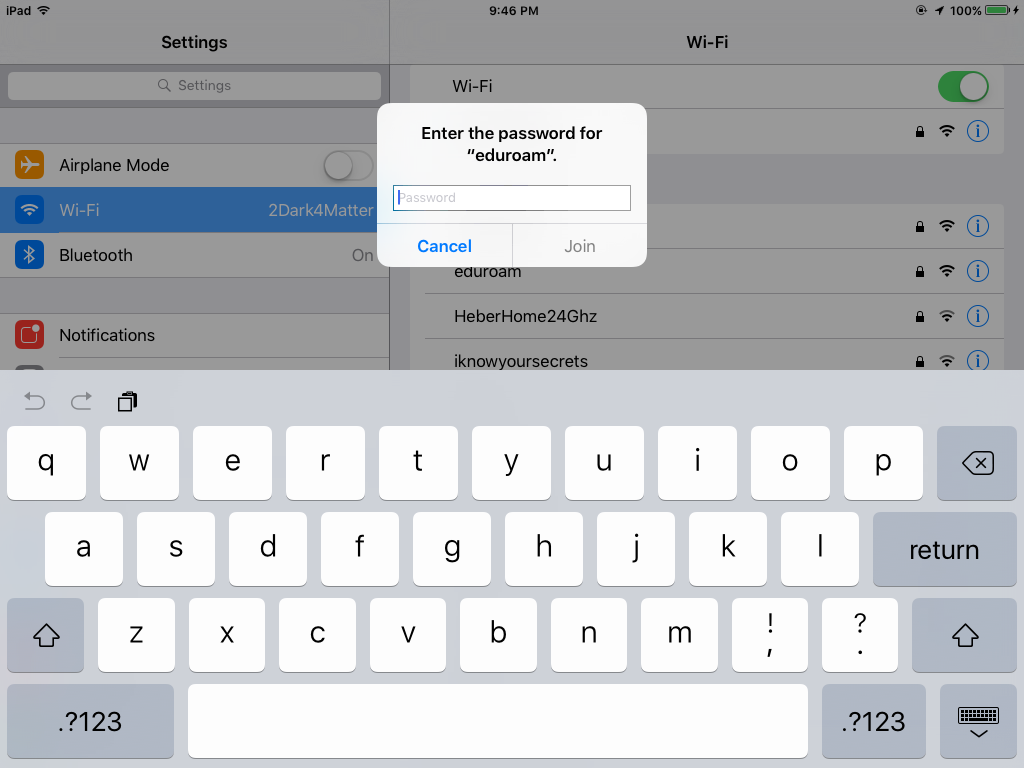
So, it was time to start the testing. First off is WPA3-Enterprise Only. Interestingly, the iPad requested the password treating it as a WPA2-PSK network. Since the network is a WPA3-Enterprise only network, no password that I enter there will work. It’s attempting to interpret the AKM that it doesn’t understand.
WPA2/WPA3 Enterprise Transition Mode
I next attempted to connect to a WPA2/WPA3-Enterprise Transition Mode network on Mist. The iPad connected without issues.
WPA3-SAE Only
Next up was to test out my home network that is configured as a WPA3-SAE Only network. I connected to it and, as expected from the experience from other devices, it treated it as a WPA2-Enterprise network. It requested my EAP credentials which is wrong. Setting my eduroam credentials won’t work with a WPA3-SAE network. Again, it is trying to interpret the AKM that it doesn’t understand.
WPA2-PSK/WPA3-SAE Transition Mode
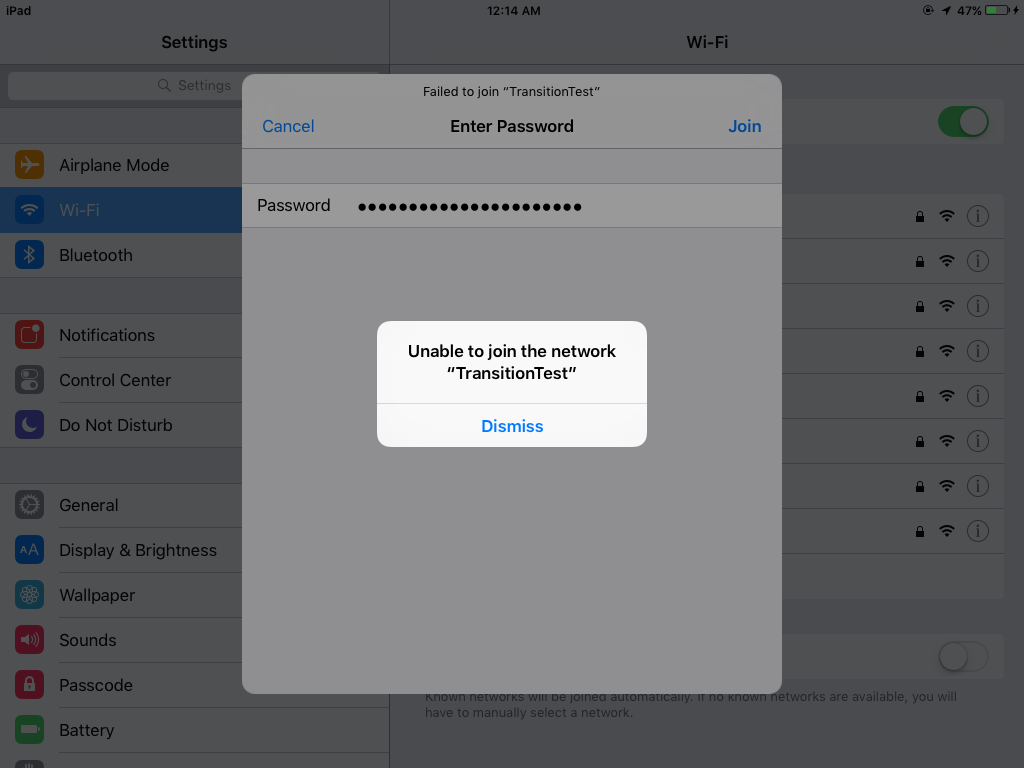
Finally, there was one more test to do. I connected it to my temporary WPA2-PSK/WPA3-SAE Transition Mode network. It requested the password as expected, but wouldn’t take my password. It gave the error below that said, ‘Unable to join the network “TransitionTest”.’ Nothing I input into the password field would work. So interestingly, WPA2-PSK/WPA3-SAE Transition Mode won’t work with this old iPad. This must be an issue with it failing because it doesn’t like having an multiple AKMs with one that it doesn’t understand.
Apple TV Gen 3
I have an old Apple TV Gen 3 sitting around that the Apple Documentation says is not supported with either WPA3-SAE or PMF. At my K12 school districts, I have schools that are still using these for Airplay devices to display their Macbooks and iPads on projector screens. My schools are slowly replacing them with newer versions, but several of these Apple TV 3’s still exist on my networks.

I pushed the eduroam mobileconfig profile using Apple Configurator to ease the install of the certificates and the eduroam profile. I then tested it using a regular WPA2-Enterprise eduroam network. The device connected without issue. So I knew the mobileconfig worked. It was time to test out WPA3-Enterprise and WPA3-SAE.
WPA3-Enterprise Only
I then decided to test an eduroam network with WPA3-Enterprise Only. I got a generic error. “There was a problem connecting to the network. The Wi-Fi password you entered is not correct. Try again. (-100)” Just as with all the other Apple devices, it appears to be treating the network as a PSK network not the as a 802.1X network.
It showed the eduroam network as below. Usually when it is connected or is a previously connected network, it will show a “>” next to the SSID and places the SSID at the top of the list. This signifies that it doesn’t know how to connect to this SSID.
WPA2/WPA3-Enterprise Transition Mode
I then attempted to join it to a WPA2/WPA3-Enterprise Transition network on Mist. Luckily this worked! It successfully connected to the WPA2/3-Enterprise Transition Mode network. Once again Transition Mode works great with WPA3-Enterprise because they are so close.
WPA3-SAE Only
I then attempted to join a WPA3-SAE only network, and it failed as expected. It gave me the same generic error, shown below, as a WPA3-Enterprise only network above. It doesn’t know how to handle the unknown AKM.
Then I attempted to join a WPA2-PSK/WPA3-SAE Transition Mode Network.
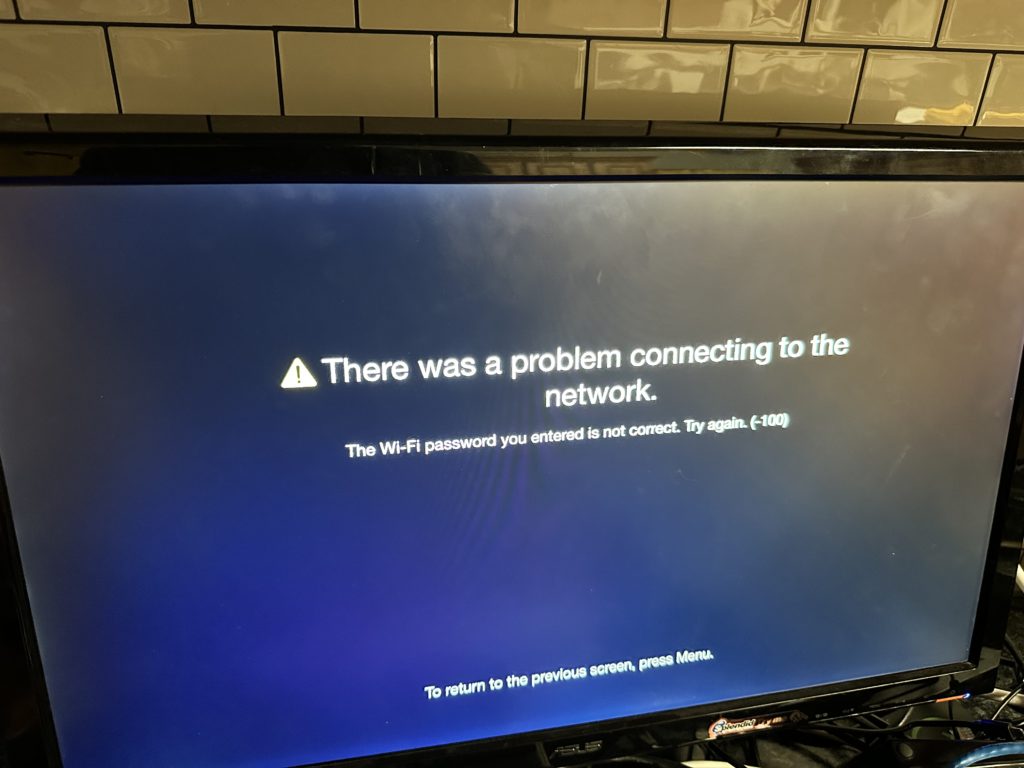
WPA2-PSK/WPA3-SAE Transition Mode
When I attempted to connect to the WPA2-PSK/WPA3-SAE Transition Mode network it failed with the generic error as before. It must not like the multiple AKMs that come with Transition Mode. Like the iPad Mini above this is the second device that I’ve found that doesn’t support the multiple AKMs!
Apple Device Findings
So, I found a device that doesn’t support WPA3-Enterprise. They are an eleven year old device or older. Is that going to be used on a University’s network? That’s debatable. Newer Apple devices may not support WPA3-Enterprise or WPA3-SAE. I don’t have an extensive list of devices with various versions to test.
It is possible, that a student, like my brother, that is trying to save money to pay for school may still be rocking an old iPhone 6 or 2012 MacBook. Since they are not tech savvy, they may have not updated it past iOS 11.2 or OS X 10.11.5. Be prepared for that trouble ticket.
There is an argument to be made that iOS 11.2 and El Capitan OS X 10.11.5 are old devices and versions. I don’t have any numbers on how many are still in use, but they still exist. That’s the issue with BYOD networks, like eduroam, when we have zero control over the clients.
Windows

I have an old Windows Surface RT that is running Windows 8.1 and cannot be updated. The Surface RT is Microsoft’s first attempt at a ARM based device. It would only run certain applications made for ARM and you had to install most of them through the Windows Store. Wes Purvis, in one of the Juniper webinars, said that he had tested a Windows Surface and had troubles. Gertjan Scharloo called it out in his Tweet below.
Because of that comment, I figure this device wouldn’t support WPA3-Enterprise and PMF. So, I decided to test it. On such an old device that doesn’t get updates, Internet Explorer struggled with connecting to most websites. Since I could use an USB drive, I was able to get the certificate on this device fairly easily. Using a USB device, I transferred over and installed the certificate. I then created the eduroam network under Network and Sharing Center. Real world, this device is most likely not going to be used on an eduroam network, but it does give us some insights to Windows 8.1 that is useful. It sounds like some newer Microsoft Surfaces do not support WPA3-Enterprise or WPA3-SAE either.
Windows 8.1
WPA2-Enterprise Only
In Mist, I set eduroam to be WPA2-Enterprise only and attempted to connect. The Surface RT connected without issue.
WPA3-Enterprise Only
Next, I wanted to test WPA3-Enterprise only. I changed the settings in Mist to WPA3-Enterprise only without Transition Mode. I then connected the Surface RT to eduroam. After trying for about 30 seconds it failed. It said “Can’t connect to this network”. So, like I guessed, the Surface RT doesn’t support WPA3-Enterprise only.
WPA2/WPA3-Enterprise Transition Mode
Next, I wanted to test to see if the device would join eduroam if the WPA2-Enterprise/WPA3-Enterprise Transition Mode checkbox was checked in Mist. I set the “Enable WPA3+WPA2 Transition checkbox” and tried to connect the Surface RT to eduroam. After a few seconds, the device joined without issue. I got a successful “Connected” message. So, if we set WPA2-Enterprise/WPA3-Enterprise Transition Mode, the Surface RT will connect. I suspect other Windows devices that don’t support WPA3-Enterprise and PMF would do the same. Especially anything running the later versions of Windows 10 or newer.
WPA3-SAE Only
Next, I wanted to see how the device would react on a WPA3-SAE only network. I clicked on my home network that is set to WPA3-SAE and got the following unhelpful and un-descriptive error message: “Can’t connect to this network”. It wouldn’t connect. No support for WPA3-SAE.
WPA2-PSK/WPA3-SAE Transition Mode
Finally, as before, I tested the Windows Surface RT against WPA2-PSK/WPA3-SAE Transition Mode. The device connected as expected without an issue. Once again, Transition Mode works on this device that doesn’t support WPA3 and WPA3-Enterprise.
So, after this test on a really old Windows device, I now have a Windows test device that doesn’t support WPA3-Enterprise only. This is good news showing that WPA2/WPA3-Enterprise Transition Mode solves any potential issues on Windows machines. It isn’t even showing issues with the different AKMs.
Toshiba L775
I have a Toshiba Windows Laptop that I still use from time to time. It is running Windows 10 Pro 1903. I decided to see how this device would handle the different security types.
First off, I just wanted to connect it to eduroam with WPA2-Enterprise. As expected, it connected without issues.
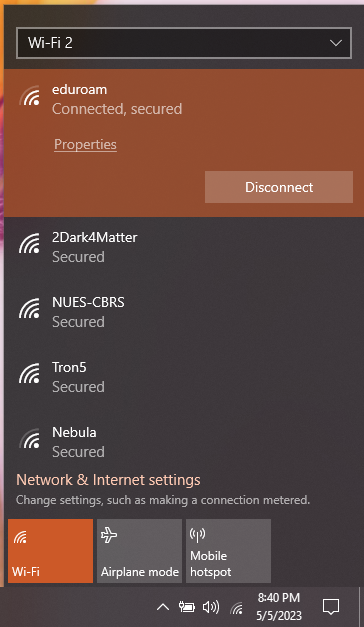
WPA3-Enterprise Only
Next up was to test eduroam running as WPA3-Enterprise Only. It connected without issue, although it was struggling to get an IP Address so it showed “No Internet, secured”. Oddly, it was connected but wasn’t getting a DHCP address.
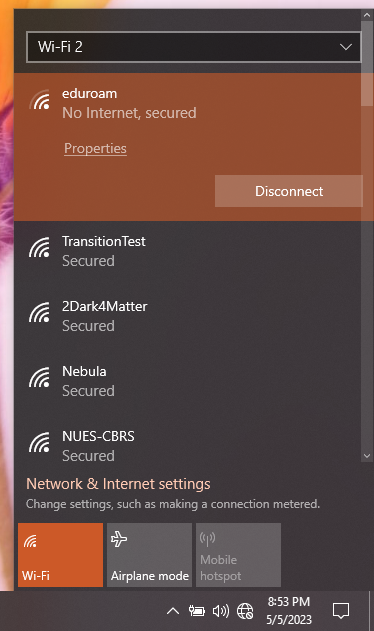
WPA2/WPA3-Enterprise Transition Mode
Next up was testing eduroam with WPA2/WPA3-Enterprise Transition Mode. It failed by saying “Can’t connect to this network”. It looks like this laptop doesn’t like the two different 802.1X AKMs for WPA2-Enterprise and WPA3-Enterprise.
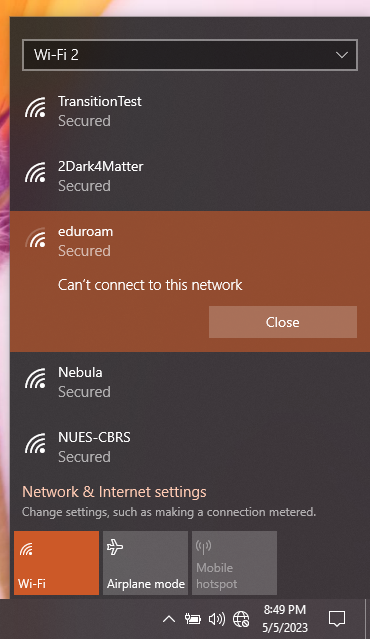
WPA3-SAE Only
Now I wanted to test just regular WPA3-SAE. I connected it to my home WPA3-SAE only network. It failed just like WPA3-Enterprise Transition Mode did, with the cryptic error “Can’t connect to this network”. It doesn’t understand the WPA3-SAE AKM.
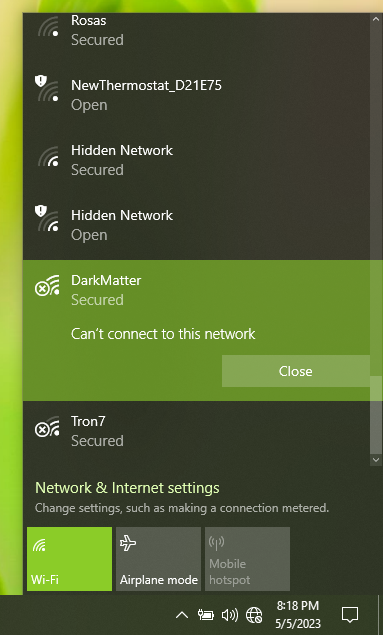
WPA2-PSK/WPA3-SAE Transition Mode
Finally, all that was left was to test my WPA2-PSK/WPA3-SAE Transition Mode SSID. Just like the WPA3-Enterprise Transition Mode and WPA3-SAE Only SSID tests, it failed with the same “Can’t connect to this network” error.
So, this laptop shows an interesting viewpoint. It supports PMF so it would connect to WPA3-Enterprise without issue since WPA3-Enterprise is just WPA2-Enterprise with PMF being required. Very interestingly, it would not connect to WPA3-SAE Only or ANY of the Transition Modes.
This laptop is running an older version of Windows 10 that was released in 2019. This version of Windows could still be running on our eduroam networks.
A quick web search, shows that Windows added support for WPA3-SAE with the Windows 10 2004 update that was released in May 2020. Updating this device to the 2004 update should fix these issues. Obviously, this laptop won’t run Windows 11. Anything that runs Windows 11 should support WPA3-SAE and WPA3-Enterprise, as long as the network card and drivers support it, which should be the majority of modern devices.
I installed the latest version of Windows 10 that is newer than the 2004 version. Interestingly, the WPA3-SAE only network still wouldn’t connect. It gave the same error, “Can’t connect to this network”. It seems the network card and driver still do not support WPA3-SAE only.
The update fixed the multiple AKM errors with WPA2-PSK/WPA3-SAE Transition Mode and WPA2-Enterprise/WPA3-Enterprise Transition Mode issues. Both the Transition Mode eduroam and Transition Mode WPA2/WPA3 SSID connected without issues, once the version of Windows was updated.
This device shows that there isn’t a solution that solves all the issues with eduroam. Transition Modes aren’t the complete solution because they can cause issues that doesn’t happen with regular WPA3-Enterprise because of issues with multiple AKMs. The issues are hardware and driver based, not just the version of the operating system. Updating the OS, if an update is available, and using Transition Modes are the best solution, especially if you are using WPA3-Enterprise with networks like eduroam. It may not solve everything though.
Android Samsung Galaxy Note 3
I have an old Samsung Galaxy Note 3. The Note 3 runs Android 5 Lollipop. Wes Purvis mentioned that Android 9 or older doesn’t support WPA3. Let’s find out about how a really old device running Android 5 supports WPA3-Enterprise and WPA3-SAE.

I found some very enlightening insights during this test. Getting a device installed with the necessary certificates is getting challenging especially with older devices. In my regular job, Android is known as the hardest client to get the eduroam certificates installed on. So, I expected a challenge. I didn’t realize the challenge would be this hard.
For my office, I have been migrating from EAP-PEAP to EAP-TLS. With PEAP, you only have to install a server side certificate on a device. With EAP-TLS you have to install a device certificate as well. I attempted multiple ways to transfer the certificates to the device, and hit stumbling blocks.
Since the Note 3 is such an old device, web browsers do not work the greatest. I tried installing the geteduroam app and couldn’t use the Google Play Store. I tried using the eduroam CAT Tool. I tried transferring the files with Dropbox and Google Drive. Nothing worked. I eventually had to transfer the file with a personal website. I’m sure newer devices up to Android 9 are different than the Note 3 with their browser support. In the real world, only newer devices, than the Note 3, should be in use on our networks.
After a lot of work, luckily, I was finally able to get the eduroam certificates installed on the Note 3. I setup eduroam to operate with WPA2-Enterprise only. The Note 3 connected without issue as expected.
WPA3-Enterprise Only
I then turned on WPA3-Enterprise only and attempted to join it to eduroam. When first connecting, things looked as expected like above.
Then things got interesting. Instead of going through the expected “Connecting..” animation, it just immediately jumped back to the Wi-Fi page. It then showed the screenshot below. The eduroam SSID shows “Saved, Secured” below.. Not connecting, nothing. I just fails without even throwing an error.
WPA2/WPA3-Enterprise Transition Mode
Next, I wanted to test out WPA2/WPA3-Enterprise Transition Mode. I set Mist to Enable WPA3+WPA2 Transition and attempted to connect the Note 3 to eduroam. Success! The Wi-Fi eduroam network showed a “Connected” message! As suspected, Transition Mode works on a really old device that is running Android 5 Lollipop. It may work the same on newer Android devices that do not support WPA3-Enterprise.

WPA3-SAE Only
I noticed the DarkMatter network below showed “Open”. That is my home network that is running WPA3-SAE without transition mode.



I attempted to connect to it. It gave me this error below, which is the typical message Android 5 gives when connecting to an Open network. Since I hadn’t connected to it before, it didn’t show an error about being a different security type.

It would not connect to the WPA3-SAE network. It did just like eduroam above when connecting to WPA3-Enterprise. It just went back to the Wi-Fi screen that shows all the networks. It didn’t say Saved and Secured, it just showed as Open.
WPA2-PSK/WPA3-SAE Transition Mode
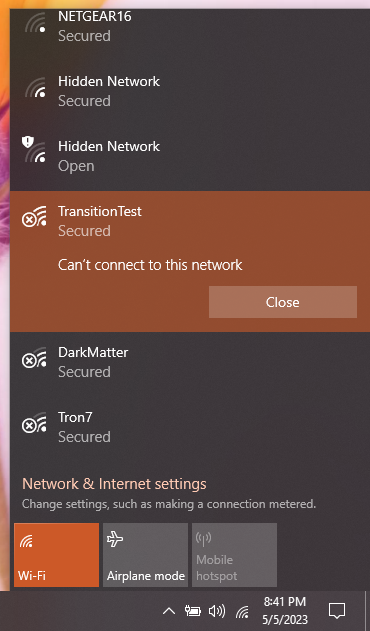
The last test I attempted was to connect to the TransitionTest SSID running WPA2/WPA3 Transition Mode. The Note 3 connected without issue.
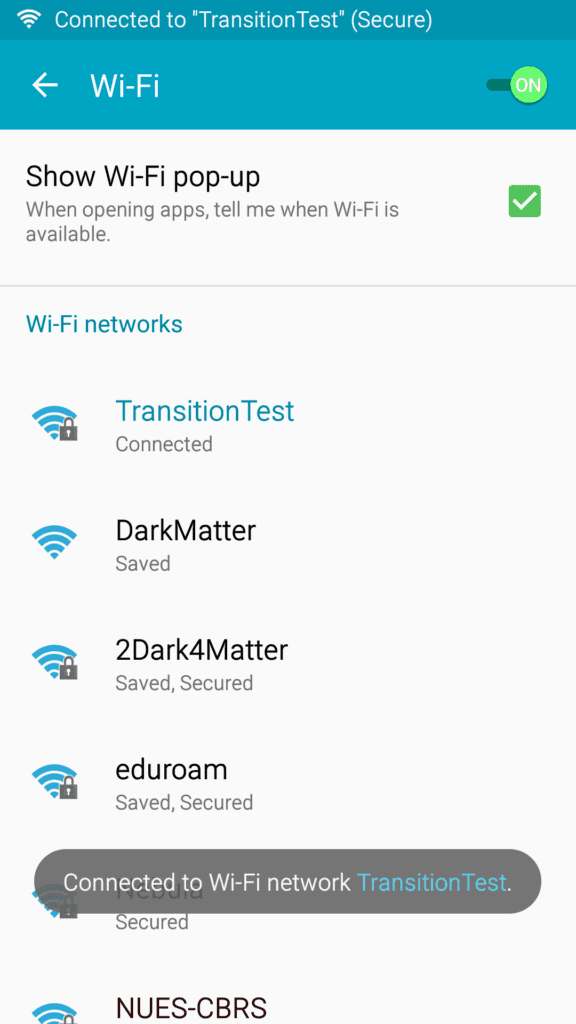

Once again, Transition Mode on both WPA2/WPA3-Enterprise and WPA2-PSK/WPA3-SAE solves the problem.
Newer Android devices may act similarly to the Note 3 or they may operate differently. The Note 3 doesn’t run the pure version of Android 5 Lollipop. So, the pure version of Android may operate slightly differently. No matter that, this test shows how Android operates if it doesn’t support WPA3-Enterprise and PMF.
Google Nexus 7 Tablet
Next up, I have a Nexus 7 Tablet sitting around that I decided to test. It is running the pure version of Android 6 Marshmallow.


I easily installed the certificates on the Android Nexus 7, like I did with the Samsung Note 3 above. I then connected to WPA2-Enterprise eduroam and there was no issues.
WPA3-Enterprise Only
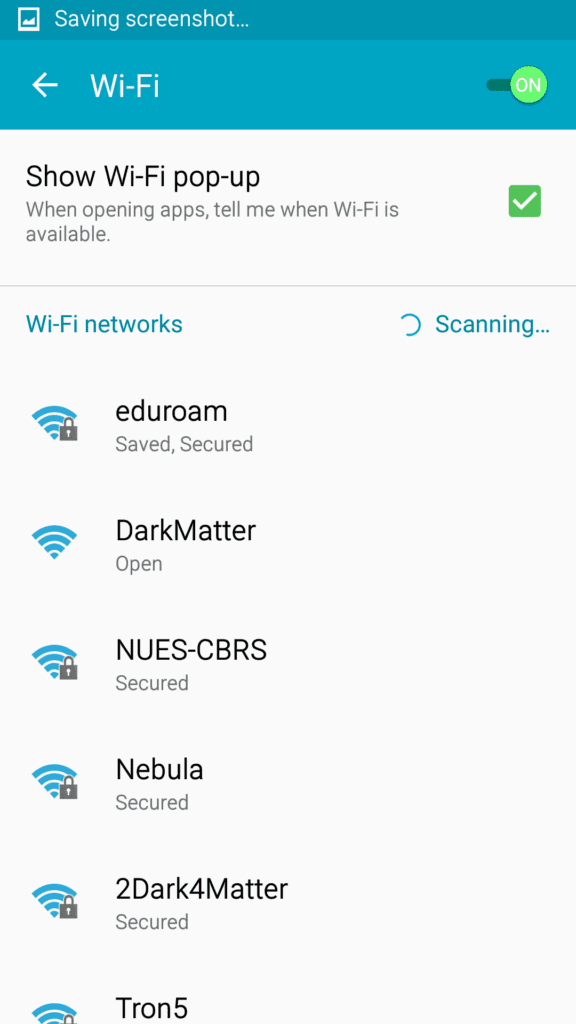
I switched eduroam to WPA3-Enterprise Only and it won’t connect. When you tapped on the eduroam SSID, it would immediately say “Saved” but would never try to connect like the screenshot below. It won’t connect to eduroam.
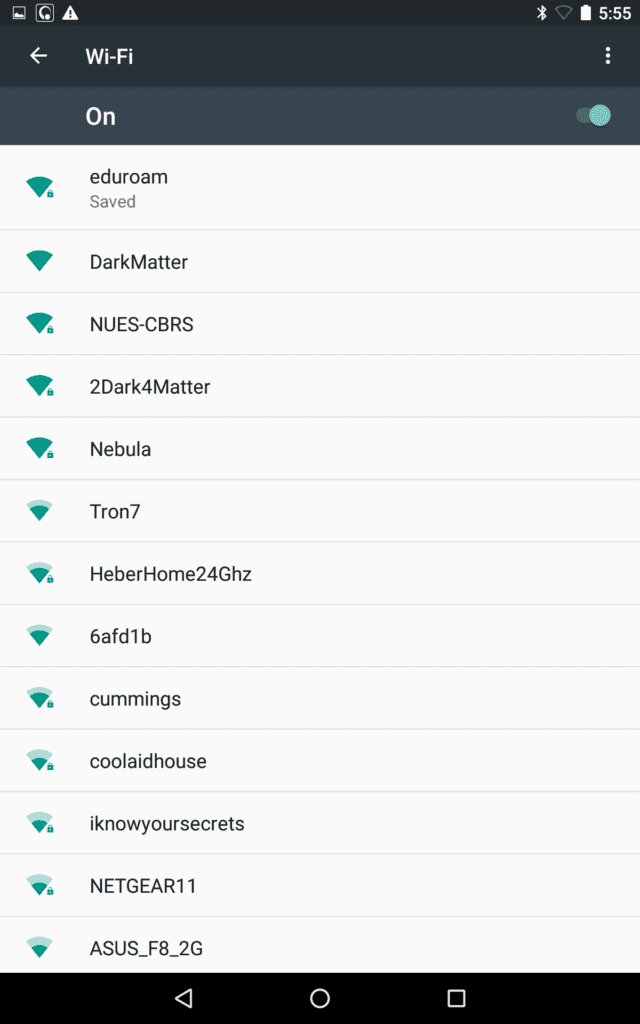

If you tapped and held, you would get the message below. If it was identifying the network correctly, it would say that Security “802.1x EAP” network. It just showed a blank white box with the eduroam SSID, with FORGET, CANCEL, and CONNECT buttons. It doesn’t know how to interpret the WPA3-Enterprise AKM.
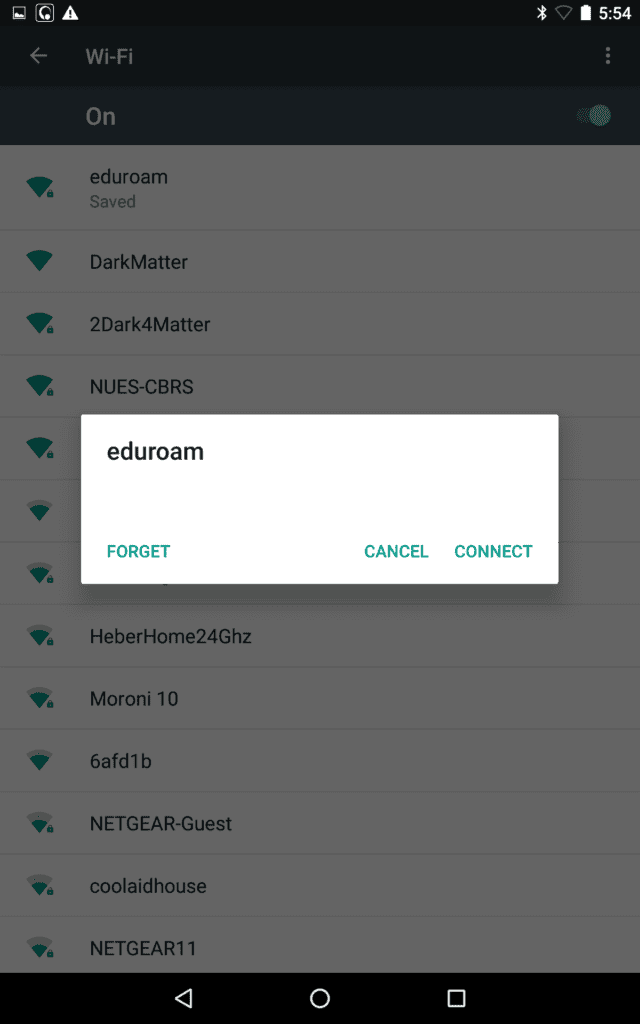

WPA2/WPA3-Enterprise Transition Mode
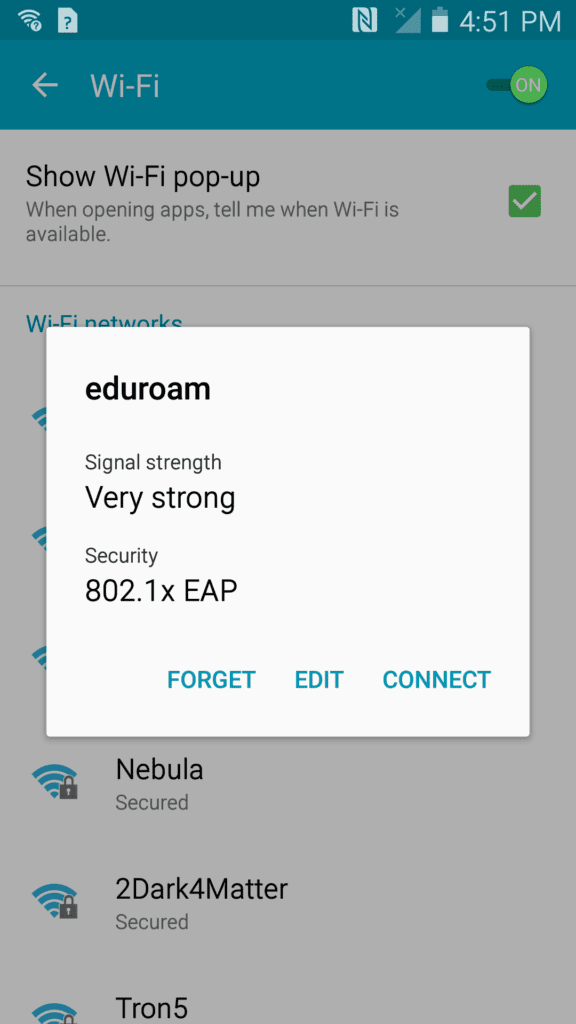
Next, I turned eduroam to WPA3-Enterprise Transition Mode. When I went to connect, it actually started to connect and gave me the proper white box unlike above. The pop up gave the eduroam SSID, status, signal strength, and Security was “802.1x EAP” as expected as you can see below. The device connected without issue with Transition Mode enabled.
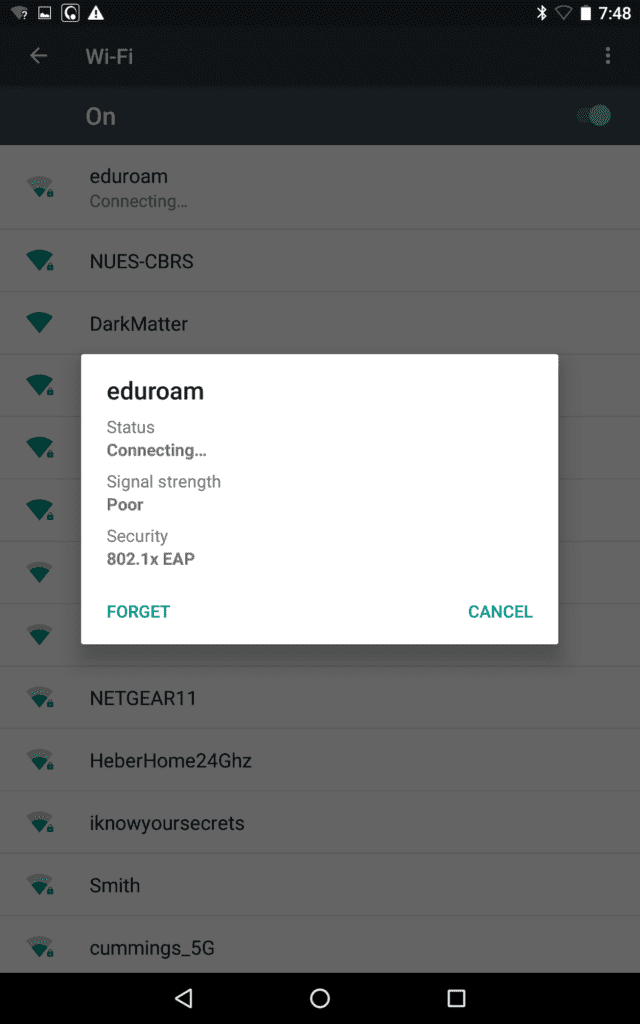

WPA3-SAE Only
Next, I attempted to connect the Nexus 7 to my WPA3-SAE only network. Just like WPA3-Enterprise only above, it wouldn’t even attempt to connect because it didn’t understand the WPA3 AKM. It would immediately revert to say “Saved”. If you tapped and held the SSID, you would get a similar white pop up box that said the SSID, FORGET, CANCEL, and CONNECT buttons. It won’t connect to WPA3 only.
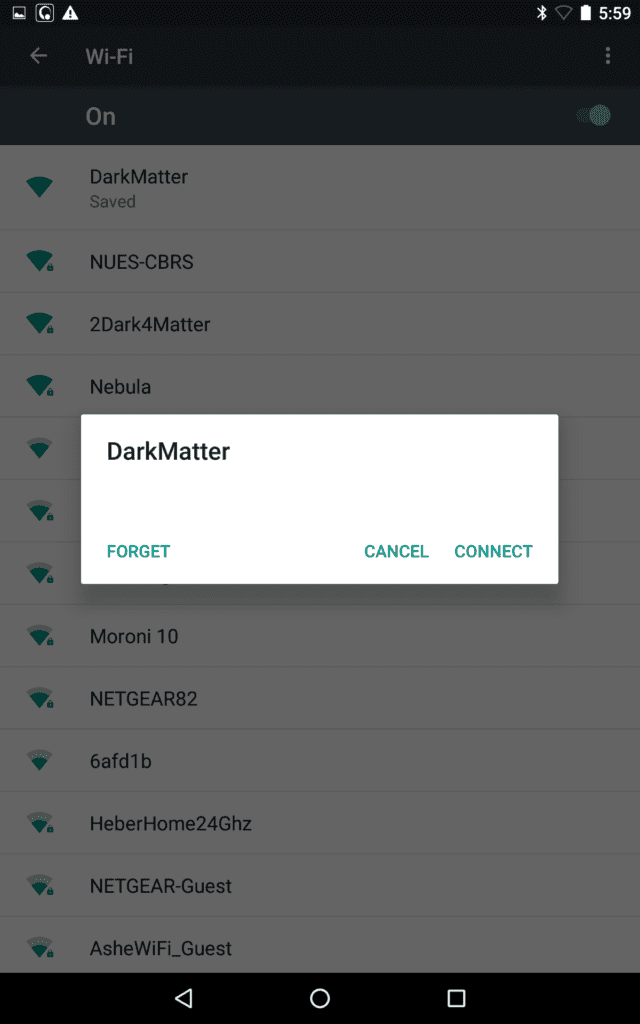

WPA2-PSK/WPA3-SAE Transition Mode
Lastly, I changed over to my test WPA2-PSK/WPA3-SAE Transition Mode SSID to see if the device would connect. Just as expected it connected without issue.
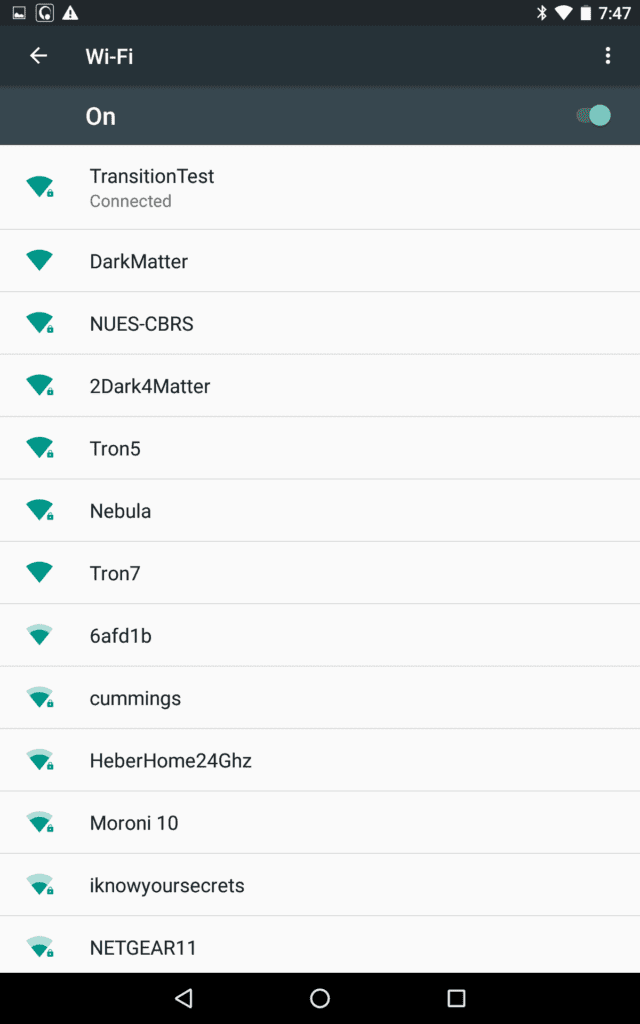

Chromebook
Finally, I have an old Chromebook and an old Chromebox sitting around since I work in K12 schools. Let’s see if they support WPA3-Enterprise and WPA3-SAE. I have an Acer Chromebook 11 that was released in 2014 and went end of life in 2019.


When it comes to Chromebooks, Google has tight control on them. Older devices have a set expiration date when they will lose access to the Chrome Management Console. These dates mean that an organization will be unable to manage the device in the Google Admin Console after that date. The device will also lose access to additional updates after that cutoff date. This makes a Chromebook an interesting device because a end of support date is built in.
Obviously, all of the devices I have tested above are end of support. ChromeOS just has an extra piece that adds to their obsolescence occurring sooner than other devices. The screenshot below has this message “This is the last automatic software and security update for this Chromebook. To get future updates, upgrade to a newer model.”
ChromeOS has automatic updating built in. So, it will force you to the latest version or at least the last supported version by the Chromebook. These reasons make it less likely that a user will be bringing a Chromebook that won’t run a version of ChromeOS that does support WPA3-SAE and WPA3-Enterprise PMF to our organizations. It is still possible just more unlikely than all the other device types that I’ve explored above.
Acer Chromebook 11
In my testing, I had an unexpected and interesting experience. When it first booted up, it had me run an update during the login. I couldn’t test out eduroam yet because of the certificates still needed to be installed. I never found out what version I was running before the update. The Chromebook had been offline for a couple years. So, I knew it was running an outdated version of ChromeOS.

The Chromebook connected just fine to my WPA2-PSK SSID; as Internet connectivity is required to login. I logged in with my Google account, and the Chromebook started to download the update. Before finishing the update it gave me an option to change the Wifi network. Since I couldn’t install the certificates for eduroam yet, I decided to test out connecting to my home SSID running WPA3-SAE.
WPA3-SAE
The connection failed with an unsuccessful message that I didn’t capture in a screenshot. When selecting the WPA3-SAE network I noticed that it said the security setting was WEP and greyed out. I couldn’t change it. It was acting like it was treating the security type as WEP because it didn’t understand the AKM of the SSID.
Seeing WEP there, makes me wonder about other clients I tested that ask for a password when they don’t understand an AKM. I’m wondering if some are defaulting to and asking for a WEP password instead of a WPA2-PSK when it encounters an AKM that it doesn’t recognize. So, it seems, some devices are reverting to WEP and not WPA2 as I had thought. I wasn’t able to take screenshots at that moment so I don’t have any pictures of what happened. I expected to be able to reproduce the issue later.
For screenshots, look at the next device below, the ASUS Chromebox. I was able to capture screenshots of it not supporting WPA3-SAE and WPA3-Enterprise for all 4 security types before it updated.

The Chromebook finished updating and rebooted. Once again, I attempted to join my home WPA3-SAE and got a the message above, with the Security field set to the correct “PSK (WPA or RSN)”. I entered the password. After a few seconds, I got a connection successful shown below. So, my guess is that during that update, it upgraded to ChromeOS that supports WPA3-SAE. There isn’t any way to rollback to a previous version, so I can’t test it again. This is a good sign though. This means the last supported version of ChromeOS for this old Chromebook supports WPA3-SAE. Other old Chromebooks, trying to join our network, might be in the same boat and their latest supported update may support WPA3-SAE.

WPA2-PSK/WPA3-SAE Transition Mode
Next, I tested to see if it could connect to a WPA2/WPA3 Transition Mode network. I connected it to my temporary TransitionTest network. The Chromebook connected without issue.

WPA2-Enterprise/WPA3-Enterprise Transition Mode
Now that I see it is connecting to WPA3-SAE, I wanted to test it on eduroam; since I can install the certificates. The fact it connected to WPA3-SAE, I’m doubted it wouldn’t connect to WPA3-Enterprise.
First, let’s test out WPA2/WPA3-Enterprise Transition Mode. I connected to eduroam and the Chromebook connected without issue.

WPA3-Enterprise Only
As the final test, I changed eduroam to full WPA3-Enterprise only. The Chromebook again connected without issue. So, the update fixed any potential issues that I might have had with this Chromebook.

While this device now supports WPA3-SAE or WPA3-Enterprise, I’m unable to show how this device was acting before the update on the Chromebox below. I didn’t expect it to finish the update and force the restart before I could fully test it.
It is good news to show that a 9 year old device that went end of life in 2019 will connect to WPA3-SAE and WPA3-Enterprise with an update. Looking at Google’s Auto Update Policy list, the oldest date that a Chromebook went end of life was 2015. The majority of Chromebooks (only about 5 are older and were largely testing devices) are running a version that have end of support dates in 2018 or newer. This Chromebook was updated last in 2019, so the vast majority of Chromebooks should support a version of ChromeOS that supports WPA3-SAE and WPA3-Enterprise. I can’t seem to find any official documentation that mention WPA3 support, but I suspect that anything going back to having support in 2018 or newer should work.
Asus Chromebox CN60
I had better luck with the Asus Chromebox to capture screenshots, since I knew what to expect. I didn’t allow the device to connect to the internet and authenticate to Google. So, it couldn’t update to the latest version of ChromeOS. I attempted to connect to each SSID security type on the login screen. ChromeOS gives enough information without connecting to identify if the device would connect or not.


WPA3-Enterprise Only
So let’s start with eduroam with full WPA3-Enterprise Only.
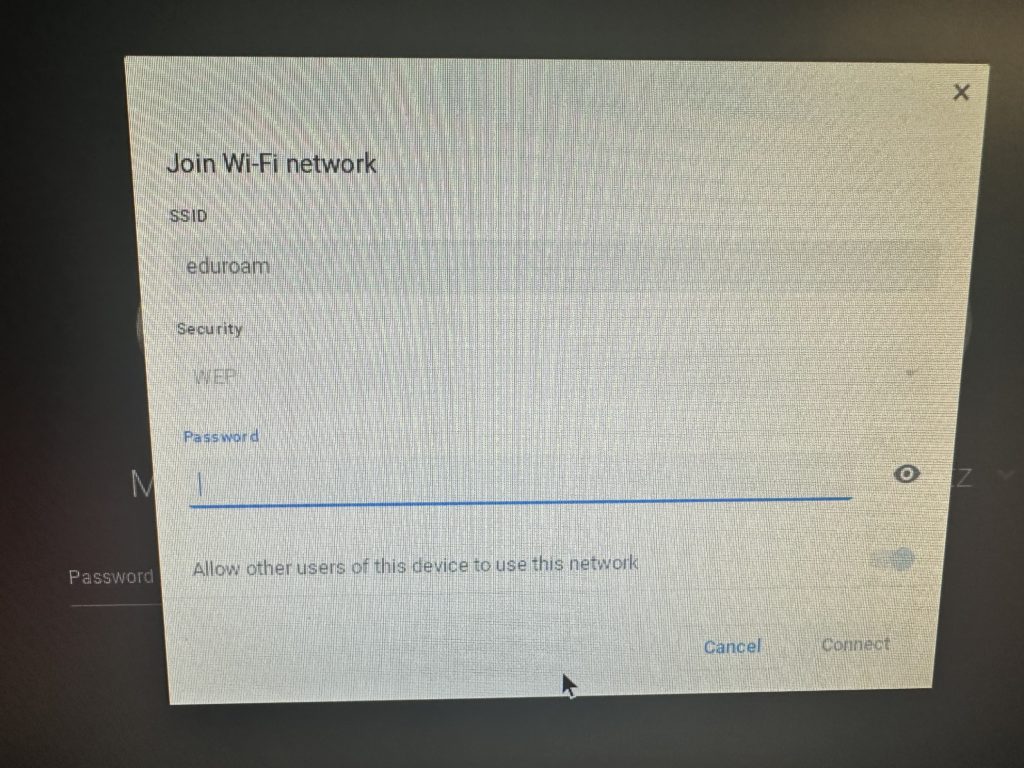

As I explained before, when I first attempt to connect the Acer Chromebook, on the login screen I attempted to show how ChromeOS interpreted the eduroam SSID AKM that it didn’t understand. As the screenshot above shows, it interprets the eduroam WPA3-Enterprise only SSID as a WEP network. That Security drop down is greyed out so you can’t change it. It also asks for a WEP Password, which obviously, no matter what is entered there will never work, since WEP and WPA3 use completely different algorithms.
WPA2/WPA3-Enteprise Transition Mode
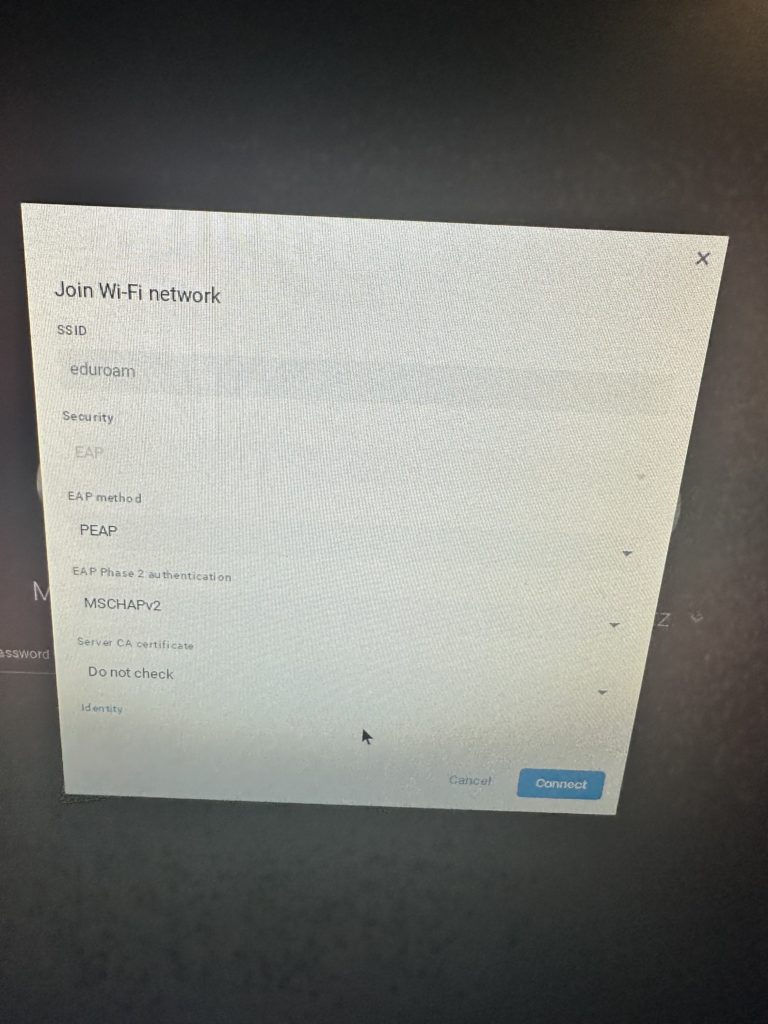

Next, I changed the eduroam SSID to WPA2/WPA3-Enterprise Transition Mode. I brought up the same menu as before and the eduroam SSID showed correctly as Security type EAP. I am then able to select the EAP Method, set the certificate, and credentials. Transition Mode works on ChromeOS that doesn’t support WPA3-Enterprise.
WPA3-SAE Only
Next let’s test out my WPA3-SAE only SSID.
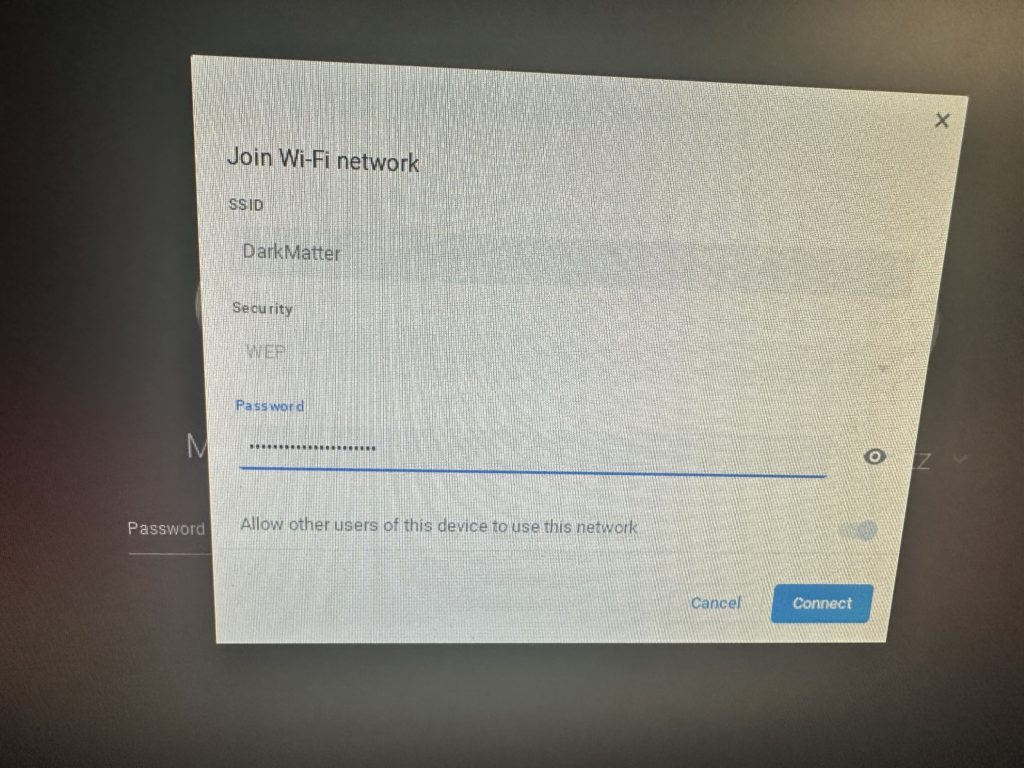

Like WPA3-Enterprise above, the Chromebox doesn’t understand the WPA3-SAE AKM. It interprets it as a WEP network that I cannot change and asks for a WEP Password. As eduroam above, nothing I enter there will work since it is asking for a WEP key and not a SAE key.
WPA2-PSK/WPA3-SAE Transition Mode
Finally, let’s test out a WPA2-PSK/WPA3-SAE Transition Mode network.
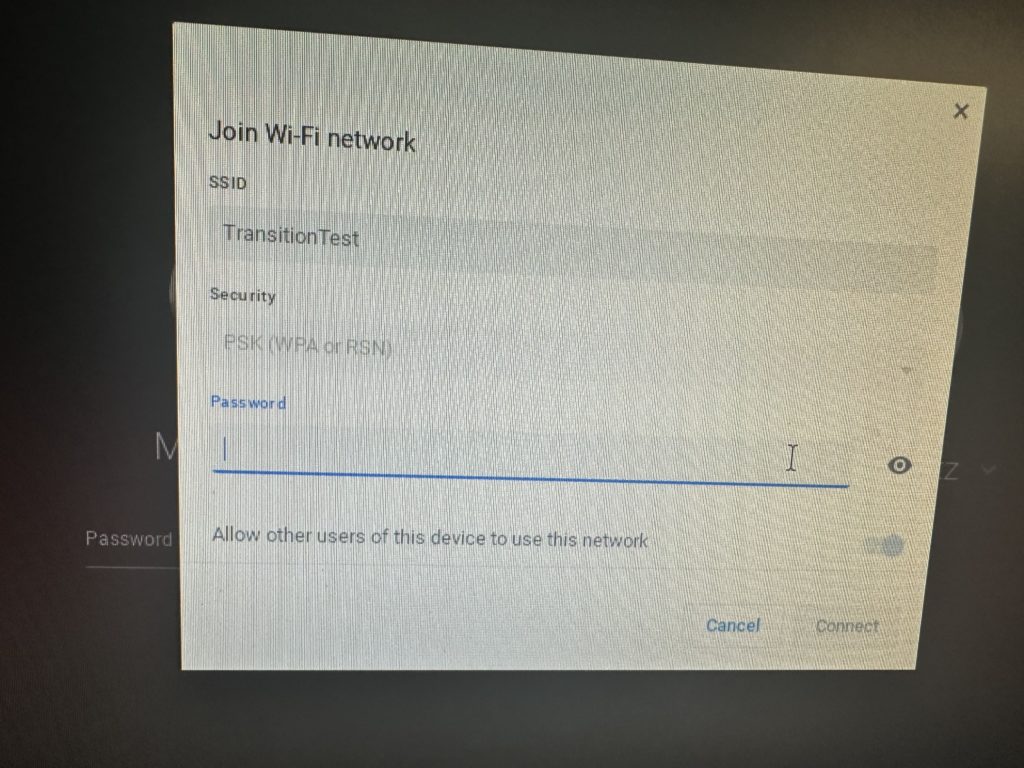

As expected, the Chromebox interpreted the Transition Mode SSID as expected. The Security mode is set to “PSK (WPA or RSN)” and is requesting a WPA2 Password. Entering the correct password in that field works as expected.
Should We Support These?
At the end of the day, how many of these devices are on our networks? We just don’t know. A guess is that there are very few if any on most networks. Turn on WPA3-Enterprise or WPA3, and you may find out fairly quickly.
In testing all this, it brought up a thought I hadn’t expected. Do we really want these devices on our networks? The Note 3 hasn’t received any security updates in years. Hence why it doesn’t support WPA3-Enterprise and PMF nor the browser doesn’t work. Granted, most eduroam networks are locked down and do not allow communication outside of internet access. Maybe we want to put these on a locked down guest network instead of our corporate networks, if we want to support them at all. That’s all things to consider.
WPA3 Protection Mechanisms
There is one more concern that I have been approached to test out, protection mechanisms in WPA3. Originally as I began my testing, I was worried that this would be an issue because these are built into the protocol. I wondered about what would happen if a client joined an eduroam WPA3-Enterprise network at their home institution when they visited a neighboring institution that hasn’t enabled WPA3-Enterprise. Would they not be able to connect, or would they get any errors?
Luckily, my worries are unfounded. After all of my testing, I have NEVER seen any protection mechanisms on WPA2/WPA3-Enterprise networks. Devices join whether they are configured for WPA2-Enterprise or WPA3-Enterprise. Most only allow you to configured the device for both or just WPA2-Enterprise.
The reason for this comes down to how close WPA2-Enterprise and WPA3-Enterprise really are to each other. It all depends on whether 802.11w or Protected Management Frames (PMF) are Required, Optional, or Disabled. That’s where all the issues with clients exists on whether or not they will work with an eduroam network running WPA3-Enterprise.
As I showed above, a Mac device that doesn’t support WPA3-Enterprise when it tries to connect to a WPA3-Enterprise network, an AKM that it doesn’t understand, will downgrade protect you from joining. It will say you’re trying to join a WPA2-PSK network. If you try joining the network it will ask you for a WPA2-PSK Passphrase, even though the SSID is set to WPA3-Enterprise.


Often, many of the MDM applications haven’t been updated to support WPA3-Enterprise, at least in the verbiage. Selecting WPA2-Enterprise will allow a client that supports 802.11w PMF to connect to a WPA3-Enterprise network without issue.
My eduroam profile was created using Apple Configurator 2 using a .mobileconfig file. It installed all the certificates for EAP-TLS for me. I set the profile to use both “WPA2 / WPA3 Enterprise” so that it would join either. Other MDM tools may not be configured to support WPA3 Enterprise yet in their verbiage. A device should join either WPA2-Enterprise or WPA3-Enterprise if you configure the network to be at least WPA2-Enterprise and the device supports PMF.

WPA2-PSK to WPA3-SAE Protection Mechanisms
The concerns about protection mechanisms are non-existent when doing WPA2/WPA3-Enterprise networks. That is different when it comes to moving between regular WPA2-PSK and WPA3-SAE.
Hypothetically, if eduroam were to use PSK and SAE, then this would be a different story. I recently began moving my Wifi network to WPA3 at home for my main client devices, such as phones, tablets, and laptops. All my IOT devices are running on different SSIDs that I’m keeping as WPA2-PSK for the time being.
When I first made the migration, my devices wouldn’t join the new network security type. I had to manually connect to the network. In so doing, I got the below error message that said, ‘”SSID” was previously joined as WPA2/WPA3 Personal, not WPA3 Personal. Are you sure you want to join this network?’
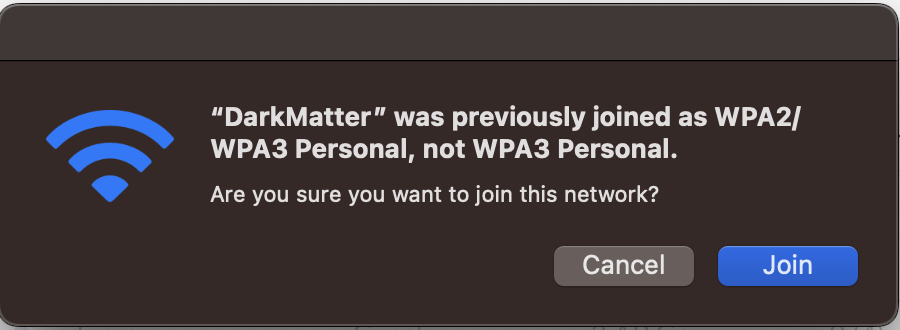

I was curious what it looked like to move back, so I moved my network back to WPA2-PSK. As before, the client wouldn’t automatically join the new security type. I had to manually join it and got the below message.
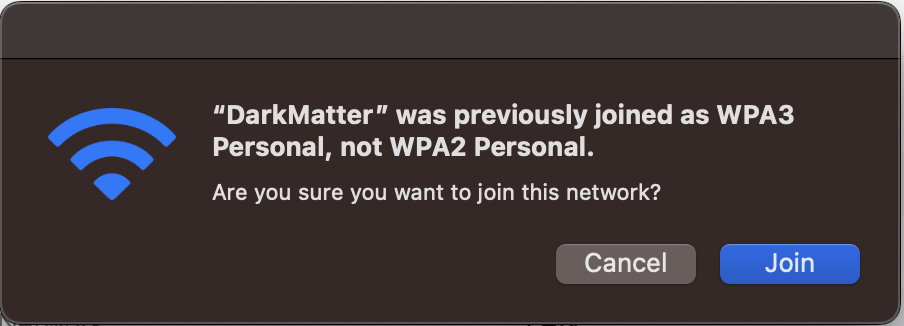

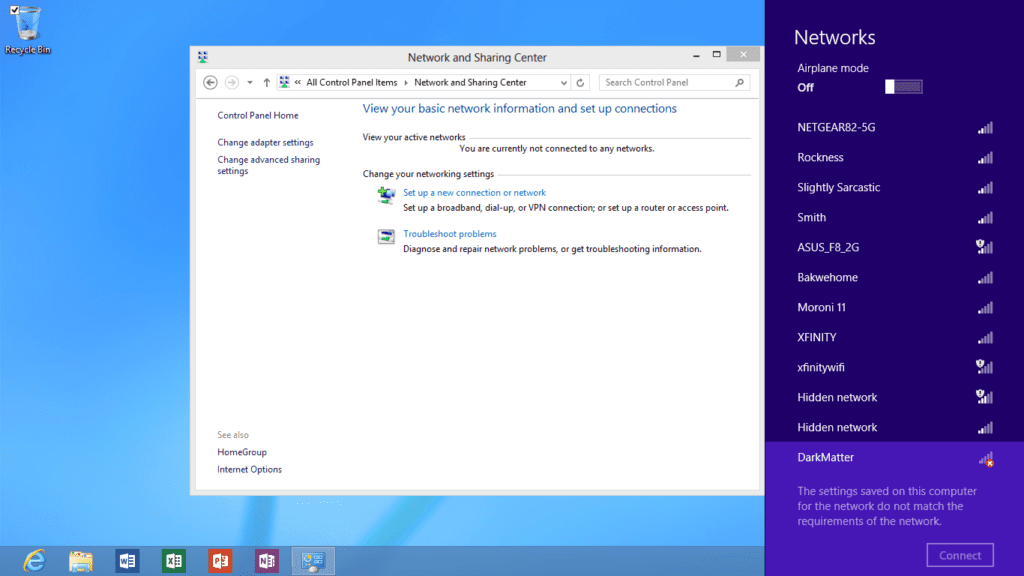
I, also, found how Windows 8.1 handles the Protection Mechanisms. When I first attempted to join my home network, that I had configured on the device previously as a WPA2-PSK network, I got the following error message:
“The settings saved on this computer for the network do not match the requirements of the network.”
It wouldn’t even let me attempt to connect to the network as the Connect button was greyed out.

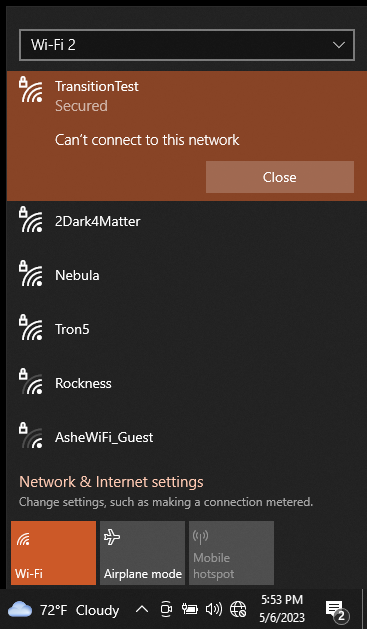
Windows 10 was slightly different with how it responded to a Downgrade Protection. It gave the same cryptic message, “Can’t connect to this network”, as when it couldn’t connect to WPA3-SAE or the Transition Modes above. To connect the device, you have to go into the Wifi settings and forget the SSID, then rejoin it.

Because of Downgrade Protection Mechanisms a device that has been configured for WPA2 is not going to immediately move to a WPA3 network, at least without accepting the move or vice versa. I had to accept that message on My Mac before it would join the new WPA3-SAE network. In the case of the Windows Surface RT, I had to forget the old WPA2-PSK network before rejoining the new WPA3-SAE network.
Next, I tested my iPhone 14 that supports WPA3-SAE and WPA3-Enterprise. I started out with connecting my iPhone to a WPA2-PSK Only SSID (I turned off Transition Mode that was being used the previous testing above.) As expected the iPhone 14 connected without issue.
Next I changed the SSID to WPA3-SAE and attempted to connect. I forgot to disconnect my device before making the change, and as soon as the change was configured, the iPhone disconnected. I then attempted to join the WPA3-SAE SSID and got the error below that said, ‘Unable to join the network “TransitionTest”‘.
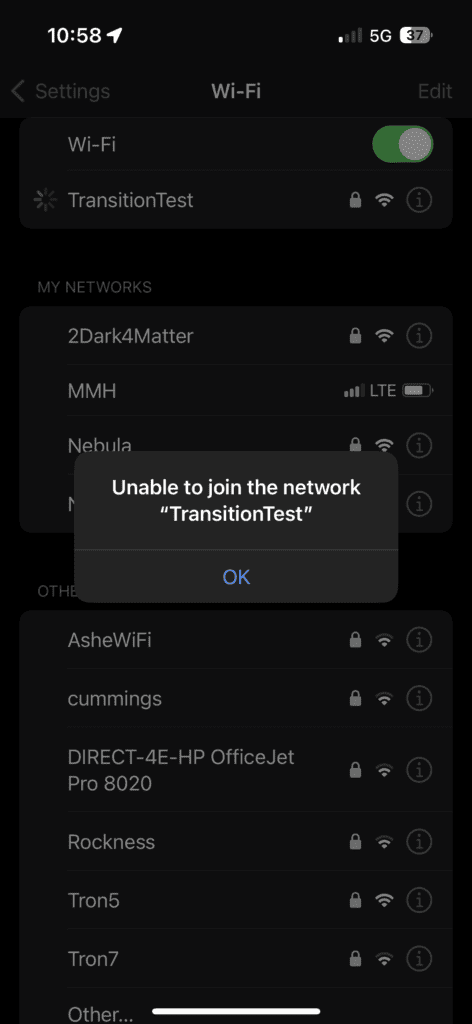

My iPad Pro 2022 did the same thing as my iPhone 14 on both going from WPA2-PSK to WPA3-SAE and the opposite. It gave the exact same error message, ‘Unable to join the network “TransitionTest”‘. This is how iOS and iPadOS handle the Downgrade Protection Mechanisms.
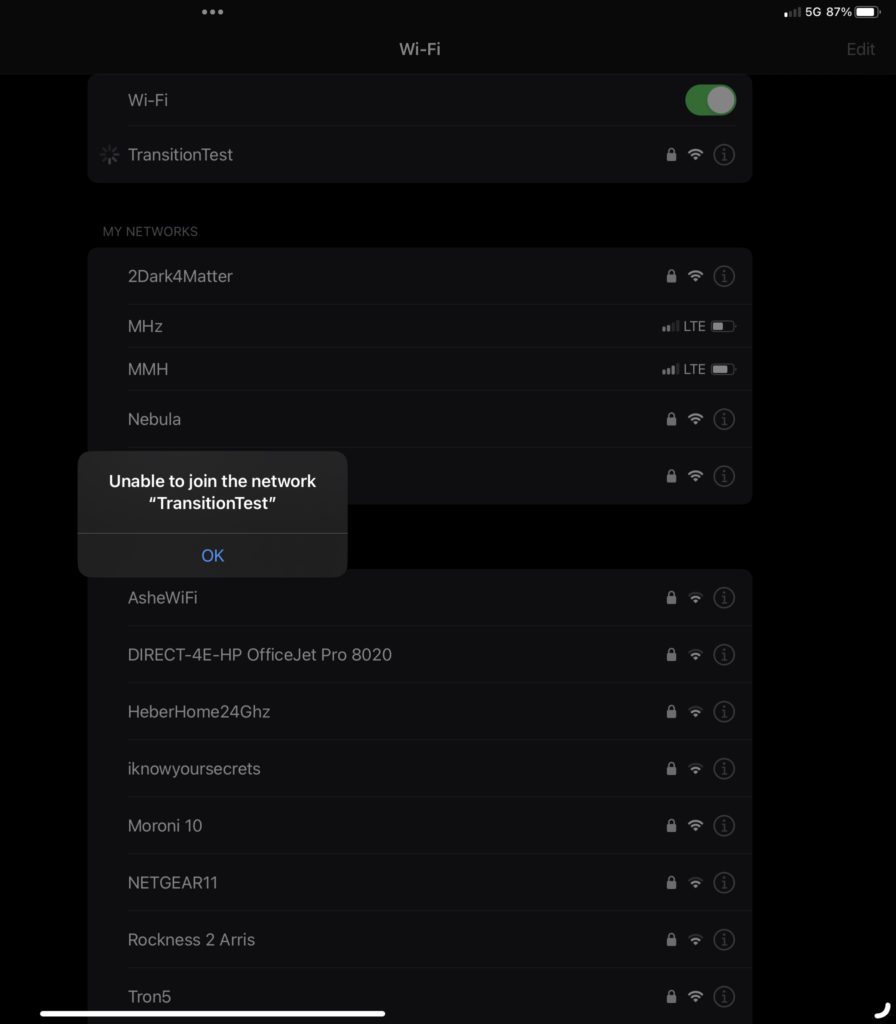

ChromeOS gave me the error below when transitioning from WPA3-SAE to WPA2-PSK. My Chromebook, that now supports both WPA3-SAE and WPA3-Enterprise, would not connect when dropping back to a WPA2 SSID. It gave an “Error configuring network” message.
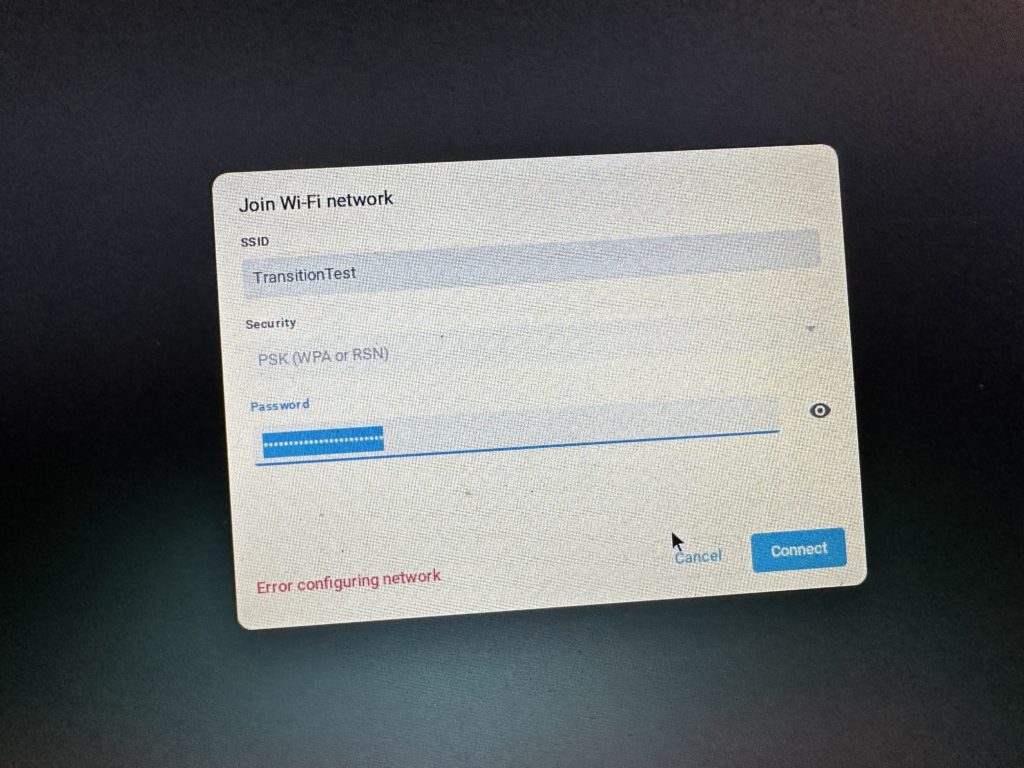

As I mentioned before, this DOES NOT HAPPEN on WPA3-Enterprise networks. This is a WPA2-PSK to WPA3-SAE or vice versa ONLY thing. The concerns about joining an eduroam network, I mentioned at the beginning of this post, are not an issue.
Client Device Spreadsheet
I put all the test results in a Google Sheet. If you have devices that you want to test with the above different security types, send me the details and I’ll add them to this list.
Obsolete Software and Hardware
I want to make one final point. Recently, there was several posts that hit my news feed about how Apple will stop supporting versions of their applications on certain versions of their operating systems. This continued movement forward in the name of progress with software is what ultimately is removing these older devices from our networks.
As I mentioned throughout, the experience on these devices that will not support full WPA3-Enterprise or WPA3-SAE is starting to show. In many cases, we are talking about 10+ year old devices. Security vulnerabilities, browser incompatibilities, and just planned obsoleteness by vendors should remove all but a very very few of these devices from our eduroam networks within a couple years at most.
So what is the solution?
These Transition Modes are meant as a means to an end, not the end in itself. At current, because we can’t control our clients, I recommend anyone running a BYOD network such as eduroam, to enable Transition Modes where you can. Lobby your vendors that don’t support it to add the option for WPA3-Enterprise. It just adds that extra piece of mind to someone supporting a BYOD network. It may only be needed on a couple devices on your network, but that is most likely a couple less trouble tickets your support teams have to encounter.
With all that said, I highly recommend that we all move to full WPA3-Enterprise or WPA3-SAE as soon as possible. If you are running a network that doesn’t have need to support older devices, test, test, and test some more, but start the migration to WPA3-SAE and WPA3-Enterprise now. Wifi 6e and the introduction of 6GHz has pushed the industry forward. It’s time to rip the bandaid off sooner than later.
eduroam + 6GHz Conclusions
In closing out this series on eduroam and 6GHz, I ask if there is a definitive answer to this problem? At the end of the day, there isn’t one solution that solves everything. Mist and Aruba get us as close as we can get to the best solution. The Wifi standard is written and these are the rules we must follow.
If your organization is running one of those other vendors, you may have to accept that certain clients won’t connect and provide other solutions for those old or “rare devices.” You may have to use a separate guest SSID that probably already exists. That is a choice best left up to the organization of what level of risk to support. Dropping support for WPA2-Enterprise is largely “safe” as Wes Purvis said in his last webinar.
Your organization might have to be willing to accept these very few old clients, as not being able to join your eduroam and WPA3-SAE networks. While, moving forward with full WPA3-Enterprise across all the bands.
In the end, these are really old devices that I tested for these experiments. Do your own tests. Don’t take my word for what I’m finding. If you do, send me the results and I’ll add them to the spreadsheet. My device list may be pretty limited compared to yours. Find out what your Most Important Least Capable devices are and begin testing them. You may find that you are able to migrate to a new 6GHz super highway with better security sooner than you thought.


